In a chilling escalation of cyber threats, the abuse of the Interplanetary File System (IPFS) has surged, enabling malicious actors to host a wave of insidious malware and phishing kits on an unprecedented scale.
This shocking revelation has sent shockwaves through the cybersecurity community, leaving experts scrambling to combat this new breed of cybercrime.
What is IPFS? (InterPlanetary File System)
IPFS, a decentralised peer-to-peer file sharing protocol, was once hailed as a revolutionary advancement for secure, censorship-resistant data sharing. However, it has now become a double-edged sword, exploited by nefarious actors for their sinister purposes.
IPFS (InterPlanetary File System) stands as a modular suite of protocols, embodying a decentralised technology integral to the Web 3.0 ecosystem, facilitating data transfer and organization.
Unfortunately, as is the often-encountered fate of emerging technologies, malicious actors have also seized upon IPFS for their sinister purposes. They have now widely adopted IPFS within their extensive phishing campaigns.
The inception of IPFS phishing attacks can be traced back to 2022, but they have recently escalated to a new level, becoming a cornerstone of mass-targeted phishing scams.
In the subsequent sections, we delve into the intricate details of these IPFS phishing assaults, their methodologies, various attack types, pertinent statistics, and essential guidance on safeguarding oneself from such threats.
IPFS and Its Role in Phishing
IPFS serves as a valuable protocol for data storage, management, and transmission. This open-source technology empowers individuals to share and store information on the Internet in a decentralized manner, emphasising efficiency and reliability.
Through IPFS, individual systems within a network can directly exchange information, secured by Peer-to-Peer (P2P) networks, eliminating the need for intermediaries.
However, the very decentralization that makes IPFS advantageous also presents challenges, as malicious actors have found a new avenue for their exploits.
In 2022, scam artists began leveraging IPFS for phishing attacks, embedding phishing forms in HTML (HyperText Markup Language) files hosted on IPFS. To execute these attacks, they utilsed gateways as proxies, leading victims to inadvertently open these files.
The perpetrators then disseminated access links to these files via phishing emails sent through the gateway to ensnare unsuspecting targets.
The Dark Underbelly of IPFS – Statistics Overview
Security analysts have sounded the alarm, pointing to a disturbing trend of cybercriminals leveraging IPFS to evade detection. This resilient and decentralized network has become an ideal breeding ground for hosting malicious payloads, rendering traditional cybersecurity measures increasingly ineffective.
Alex Biden, a cybersecurity expert, shared his concerns, stating, “IPFS offers anonymity and resilience against takedowns, making it a haven for criminals,”
“They can distribute malware and phishing kits with impunity, and it’s extremely challenging for authorities to trace the perpetrators.”
Recent data paints a grim picture of the escalating crisis. Incidents involving malware and phishing attacks hosted on IPFS have surged by a staggering 2,566.67 percent.
These attacks target individuals, corporations, and government entities alike, stealing sensitive information, finances, and intellectual property.
The malware spread via IPFS is becoming increasingly sophisticated, exploiting previously unknown vulnerabilities and utilizing advanced evasion techniques.
Meanwhile, phishing kits hosted on IPFS are luring unsuspecting victims into providing confidential information, leading to identity theft and financial losses.
To calculate the percentage increase in IPFS phishing attempts from 2022 to February 2023, you can use the following formula:
Percentage Increase = [(New Value – Old Value) / Old Value] * 100
- Old Value (January and February 2022): 15,000 phishing attempts per day.
- New Value (February 2023): 400,000 phishing attempts in February 2023.
Now, let’s calculate the percentage increase:
Percentage Increase = [(400,000 – 15,000) / 15,000] * 100 Percentage Increase = [(385,000) / 15,000] * 100 Percentage Increase ≈ 2,566.67%
The percentage increase in IPFS phishing attempts from January and February 2022 to February 2023 is approximately 2,566.67%. This represents a significant and alarming surge in phishing activity on the IPFS network during this period.
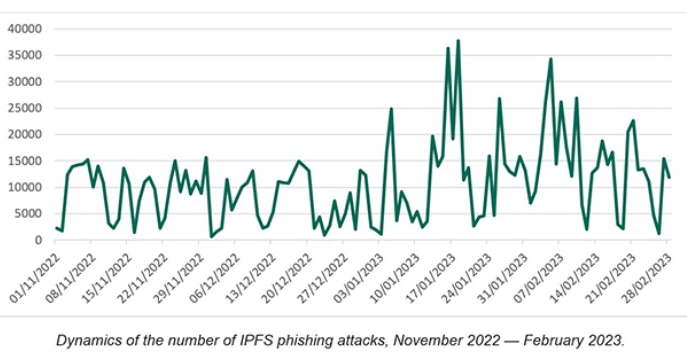
According to securelist.com in late 2022, it observed 2–15 thousand IPFS phishing letters a day for most of the time. However, there were quieter days too. Its systems registered only 637 such letters on December 1, and 937 on December 23.
Starting this year, IPFS phishing began to grow in scale. It observed a few upsurges in January and February with over 24,000 letters a day — with peaks reaching 34–37 thousand/day. However, the flurry has died down little by little by mid-February, the number of attacks mostly returning to November and December levels.
It also noted February turned out the busiest month in terms of IPFS phishing activity. In that month alone, Securelist observed almost 400,000 letters — more than 20,000 above the January figure, and over 100,000 more than in November and December 2022.
The Battle to Restore Cybersecurity
Governments and cybersecurity firms worldwide are now racing against the clock to counter this growing menace. Efforts are underway to monitor and disrupt malicious IPFS activity, but the inherent anonymity of the system makes tracking down criminals a daunting task.
Varieties of IPFS Phishing Attacks
Cyber adversaries employ diverse tactics when utilizing the IPFS network to conceal their nefarious operations. IPFS phishing attacks manifest in three prominent forms:
- Malicious URLs: Malicious actors disseminate phishing messages through emails, pop-ups, and other communication channels containing links that divert unsuspecting victims to malicious IPFS gateways.
- DNS Spoofing: Threat actors craft counterfeit Domain Name System (DNS) records, redirecting individuals to deceptive IPFS gateways, thereby obscuring their true intentions.
- SSL Certificates: Phishing perpetrators employ counterfeit Secure Sockets Layer (SSL) certificates, cunningly masking malicious websites as trustworthy ones, deceiving users into believing they are visiting secure destinations.
Leveraging the decentralized nature of IPFS, malevolent entities can establish enduring and untraceable phishing websites, persisting in their malign activities even after the initial source is removed.
Removing Phishing Pages from IPFS Content Presents Challenges
Eliminating standard phishing pages often involves reaching out to the web content provider or owner for their removal.
This process can be time-consuming, particularly when the content is hosted on bulletproof providers. These rogue hosting services explicitly state their non-compliance with law enforcement requests and content takedowns.
However, the process of taking down phishing content from IPFS differs significantly, as it necessitates the removal of the content from all nodes.
Providers of IPFS gateways attempt to counteract these fraudulent pages by periodically deleting links to such files. Nonetheless, this action doesn’t always occur as swiftly as blocking a traditional phishing website.
In fact, as of March 27, 2023, Kaspersky researcher Roman Dedenok noted that some IPFS file addresses, originating in October 2022, remained functional at the time of his report.
Distinguishing Features of IPFS Phishing Attacks
In IPFS phishing attacks, threat actors employ a distinct modus operandi. They meticulously select their targets and entice them through phishing emails, which, upon interaction, lead the victim to a counterfeit webpage meticulously crafted to pilfer their credentials or financial data.
This unique approach offers several advantages to the malicious actors. It substantially lowers hosting expenses, allowing them to operate stealthily with reduced costs.
Moreover, the distributed nature of IPFS makes the removal of fraudulent content from the internet an arduous task, as it concurrently resides on multiple systems, evading easy eradication.
Threat Actors Rapidly Adopt Web3 IPFS Technology
Palo Alto Networks detected a 178% increase in IPFS-related traffic from the last quarter of 2021 to the first quarter of 2022, while VirusTotal reported more than 6,500% increase during that same reporting period.
Researchers from Unit 42 have detected threat actors engaging in discussions related to their utilisation of IPFS, as well as their clients’ embrace Web3, with a specific focus on its applications in phishing and similar cybercriminal activities.
These threat actors frequently promote their illicit services, highlighting various advantages such as websites remaining “unsuspended online for extended periods” and the absence of “downtime in their links.”
In essence, IPFS has afforded them protection and prolonged sustainability for their campaigns, thanks to the inherent characteristics of IPFS’s decentralised file system.
Threat actors employ IPFS gateways in various ways, primarily as delivery mechanisms, infrastructure for hosting or staging payloads, and decentralized Command and Control (C2) channels.
In 2022, the following malware families made extensive use of IPFS:
- Dark Utilities: This malware family utilized IPFS gateways to stage malicious payloads.
- IPStorm: IPStorm employed IPFS gateways as a C2 channel for Peer-to-Peer (P2P) communications.
In addition to these malware families, attackers have leveraged IPFS gateways to distribute various red team tools and malware, including:
- OriginLogger
- XLoader
- XMRig
- Metasploit
Now, let’s delve into how these threats operate at a high level, specifically focusing on how IPFS facilitates their malicious activities.
OriginLogger: OriginLogger, an offshoot of the Agent Tesla remote access Trojan, has been active since 2019. This malware is coded in .NET and functions as a highly evasive information stealer. Its primary targets include capturing keystrokes and clipboard data, which are then transmitted to a server controlled by the threat actor through a C2 channel.
Unit 42 researchers discovered an email lure, cleverly disguised as an overdue invoice, featuring an XLL attachment (as depicted in Figure 19). Upon opening the XLL file, it triggers an HTTP GET request to an IPFS URL
Guarding Against IPFS Phishing Attacks: A Defense Blueprint
Researchers have outlined key measures for both individuals and businesses to fortify their defenses against IPFS phishing attacks:
- Cybersecurity Hygiene Training: Organizations are strongly advised to impart cybersecurity hygiene training to their staff. By conducting simulated phishing attacks, employees can develop the skills to distinguish phishing emails from legitimate ones, thereby enhancing the overall security posture.
- System and Network Protection Tools: Both individuals and organizations should make strategic investments in robust endpoint and mail server protection tools equipped with anti-phishing capabilities. These tools serve as a crucial line of defense, mitigating the risk of phishing emails infiltrating the network.
- Cloud Protection Tools: Users should embrace specialized anti-spam and anti-phishing tools tailored for cloud environments. These tools extend protection to cloud-based applications, communication platforms, and storage, safeguarding critical cloud data from the perils of phishing attacks.
By implementing these proactive measures, individuals and organisations can bolster their resilience against the growing threat of IPFS phishing attacks, fortifying their digital defenses in an increasingly perilous online landscape.
As the abuse of IPFS continues to rise, the world watches with bated breath, hoping that the cybersecurity community can rise to the challenge and thwart these malevolent actors.