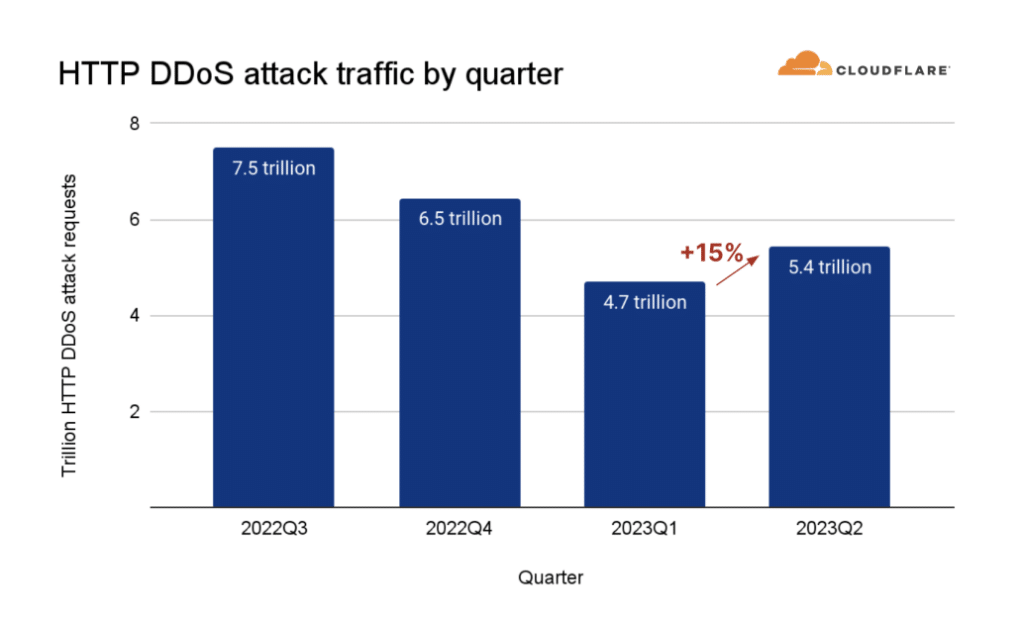
Despite having 35% decrease in year on year, HTTP DDoS attacks witnessed 15% increase in the last quarter which targets HTTP Internet properties such as websites and API gateways.
Cloudflare’s systems automatically detected and mitigated a massive DDoS attack that reached a peak of 1.4 terabits per second (Tbps) which has targeted US based internet service provider.
During the quarter, several industries and countries have been consistently targeted and have experienced significant impacts from the ongoing attacks.
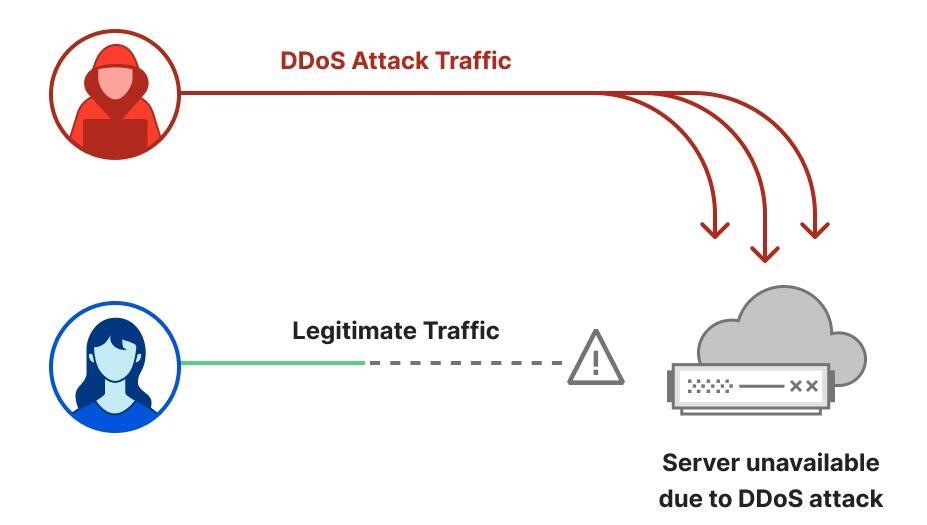
Attacks highly randomised, sophisticated & designed to bypass mitigation systems.
The threat actors responsible have skilfully replicated browser behaviour and introduced significant randomisations in properties like user-agents and JA3 fingerprints.
These operations have specifically targeted well-known companies, including a prominent VoIP provider, a leading semiconductor company, and a major payment and credit card provider, among others.
The United States ranked as the primary source of HTTP DDoS attacks in terms of attack traffic volume, followed by China in second place and Germany in third place. Approximately three out of every thousand requests observed were associated with HTTP DDoS attacks originating from the US.
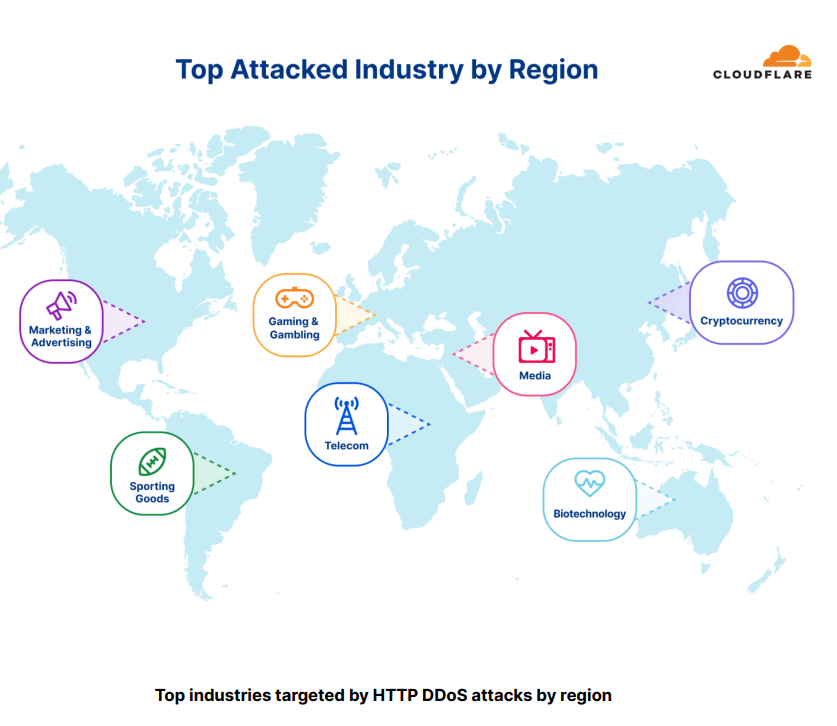
Which industries are under attack ?
During the quarter, industries such as management consulting firms, non-profit organizations, cryptocurrency, and gaming gambling websites have been consistently targeted and have experienced significant impacts from the ongoing attacks.
Among the websites protected by Cloudflare, approximately six out of every ten thousand HTTP requests directed towards cryptocurrency websites were identified as part of these attacks.
Gaming and gambling websites ranked second in terms of targeted attacks, followed closely by marketing and advertising websites in third place.
During the last quarter, non-profit organizations faced the highest number of attacks, with HTTP DDoS attacks accounting for 12% of the traffic directed towards them.
Cloudflare’s Project Galileo, which recently completed its ninth anniversary, provides protection to over 2,271 non-profit organsations across 111 countries. On a daily basis, an average of 67.7 million cyber-attacks targeted non-profit organizations, including DDoS attacks directed at LGBTQIA+ websites.
Countries and regions under attack: Examining DDoS attack targets:
In terms of total attack traffic volume, Israel experienced a significant increase in attacks last quarter, placing it as the most targeted country. However, this quarter saw a decrease of 33% in attacks on Israeli websites, resulting in Israel ranking fourth in terms of targeted attacks.
The United States has regained its position as the most attacked country, with Canada and Singapore following closely behind in second and third place respectively.
Global DDoS Attack Landscape 2023
The second quarter of 2023 witnessed a notable surge in targeted and persistent DDoS attack campaigns across various fronts. These attacks exhibited a higher level of sophistication and were directed towards specific targets. Some of the key developments during this period include:
- Deliberately engineered and targeted DNS attack
- Multiple DDoS offensives
- Attacks targeting Cryptocurrency companies
- An increase in deliberately engineered and targeted DNS attacks alongside a 532% surge in DDoS attacks exploiting the Mitel vulnerability (CVE-2022-26143). Cloudflare contributed to disclosing this zero-day vulnerability last year
- Multiple DDoS offensives orchestrated by pro-Russian hacktivist groups REvil, Killnet and Anonymous Sudan against Western interest websites.
- Attacks targeting Cryptocurrency companies increased by 600%, as a broader 15% increase in HTTP DDoS attacks was observed. Of these, we’ve noticed an alarming escalation in attack sophistication which we will cover more in depth.
While overall attack durations showed an increase, it is important to note that most attacks were short-lived, including the aforementioned ACK flood attack. However, the quarter also witnessed a significant rise of 103% in attacks that exceeded a duration of three hours.
Additonally,. Cloudflare encountered one of the largest-scale attacks—a formidable ACK flood DDoS attack. The attack originated from a Mirai-variant botnet comprising approximately 11,000 IP addresses.
Its target was an Internet Service Provider based in the United States. The attack reached a peak traffic volume of 1.4 terabits per second (Tbps). Fortunately, the robust systems employed by Cloudflare automatically detected and mitigated the attack, preventing significant disruption.
These shifts in the DDoS landscape highlight the evolving nature of these attacks. They underscore the need for heightened cybersecurity measures and constant monitoring to protect against sophisticated and targeted DDoS campaigns.
The recent rise in HTTP-based DDoS attacks serves as a reminder that despite overall improvements in cybersecurity, threats continue to evolve and adapt
They also underscore the need for ongoing investment in robust security measures and constant vigilance to ensure the stability and accessibility of internet properties in an increasingly interconnected world.
As the threat landscape continues to evolve, organisations must remain vigilant and adapt their defense strategies to effectively mitigate such attacks.
Deploying firewalls, intrusion detection systems, load balancers, and content delivery networks (CDNs) can help distribute traffic and filter out malicious requests, mitigating the impact of HTTP-based attacks.