A new generation of aggressive, layer 7 (L7), HTTPS Flood attacks, also known as Web DDoS Tsunami attacks, is disrupting the market by bypassing organisations’ traditional DDoS protection and web application firewall (WAF) solutions.
Radware (NASDAQ: RDWR) is a global leader in cybersecurity and application delivery solutions for physical, cloud, and software-defined data centers
Shira says the destructive attacks, which roll out in multiple waves, last for days, hit with ultra-high volumes, and are aimed at wearing down an organisation’s security team. They also masquerade as legitimate traffic, making them very difficult to detect and mitigate.
Recently, Radware took on one of these attacks to defend a customer and major global business after it started with a ransom demand and evolved daily with more attacks and demands.
The colossal scale and duration of this DDoS attack highlights the critical need for robust cybersecurity measures in today’s interconnected business world.
This is what was encountered:
- Ultra-high volumes: Some attack waves peaked at nearly two million requests per second (RPS).
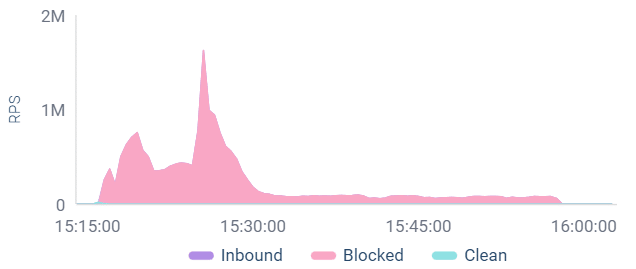
Web DDoS Tsunami attack wave peaking at nearly 2 million RPS
- Persistent and long attacks: Over the course of seven days, we observed nearly 20 different waves. Some lasted several hours, reaching over 10 billion requests in aggregate.
Persistent Web DDoS Tsunami attack wave of over 1 million RPS for almost 3 hours

- Complex attacks: They were encrypted and crafted as HTTPS GET requests, posing as legitimate web requests.
Hackers often garner attention for their staggering RPS (Requests Per Second) numbers. However, what sets apart this new breed of attack and the recent attack campaign is the perilous convergence of volume, duration, and complexity.
To defend effectively against attacks during an extended assault, relying solely on conventional rate-limiting solutions falls short. The truth is, traditional mitigation tools that rely on pre-existing signatures or rate-based detections are ill-equipped to defend against this type of hacking attempt.
Network-based DDoS protection solutions are inadequate in detecting and mitigating L7 DDoS attacks. resulting in standard on-premises or cloud-based Web Application Firewalls (WAFs) struggling to cope with the magnitude and randomness of these attacks.
Moreover, employing rate-limiting techniques can significantly impede legitimate traffic, leading to undesirable consequences such as false positives.
Consequently, businesses find themselves caught off guard. The absence of a behavioral-based approach and automated real-time signatures renders standard protections defenseless, allowing attacks to overwhelm and outsmart them, leaving businesses exposed to vulnerabilities.
While the concept of DDoS attacks is not new, the emergence of the Web DDoS Tsunami signifies a significant escalation in both the sophistication of the attacks and the audacity of the actors behind them.
It’s now become imperative for companies to acknowledge this new reality and take proactive measures to fortify their defenses against these increasingly advanced threats.
This includes behavioural-based algorithms that can automatically detect and quickly generate new signatures for unknown malicious requests at a high scale, on the fly, and in real-time without generating false positives and blocking legitimate traffic.
The level of service and support that back the solution is also important, especially now when so many security teams are running lean.
In May Gabi Malka, Radware’s chief operating officer said, “the dramatic rise in Web DDoS Tsunami attacks poses an immediate cyber threat,”
“Organisations worldwide regardless of industry have fallen victim to these attacks, leaving them confounded as to why their existing defense solutions are faltering,”
“Just because organisations have standard WAFs or network-based DDoS mitigation in place, they should not take for granted that they are adequately protected,” Malka said
The Rise In Web DDoS Tsunamis
The rise in Web DDoS Tsunamis has resulted in a greater need for advanced L7 DDoS detection and mitigation measures. In recent campaigns, hackers have been orchestrating large-scale attacks by combining network and application layer techniques, employing new tools to generate massive request-per-second (RPS) Web DDoS attacks.
According to Cloudflare, in Q3 of 2022 online industries received the most application-layer DDoS attacks, recording a 131 percent increase quarter-on-quarter (and 300 percent year on year) rise in the number of attacks.
To evade detection, these L7 DDoS attacks cleverly mimic legitimate traffic and utilize various evasion techniques, including the randomisation of HTTP headers, cookies and, IP spoofing,
As the threat landscape continues to evolve, cybersecurity experts have emphasized the importance of staying ahead by continuously adapting and investing in robust defense mechanisms.
By embracing cutting-edge mitigation solutions and leveraging the expertise of security professionals, organisations can effectively combat the ever-growing risk posed by DDoS attacks







