Infoblox Inc today published a second threat report with critical updates on “Decoy Dog,” the remote access trojan (RAT) toolkit they discovered and disclosed in April 2023.
The malware uses DNS to establish command and control (C2) and is suspected as a secret tool used in ongoing nation-state cyber attacks.
The threat actors swiftly responded following Infoblox’s disclosure of the toolkit, adapting their systems to ensure continued operations, indicating that maintaining access to victim devices remains a high priority.
The analysis indicates a notable expansion in the use of the malware, with a minimum of three actors currently using it. Despite its foundation on the open-source RAT Pupy, Decoy Dog represents an entirely novel and previously undiscovered form of malware, boasting numerous features that enable it to establish persistence on compromised devices.
Decoy Dog Activity
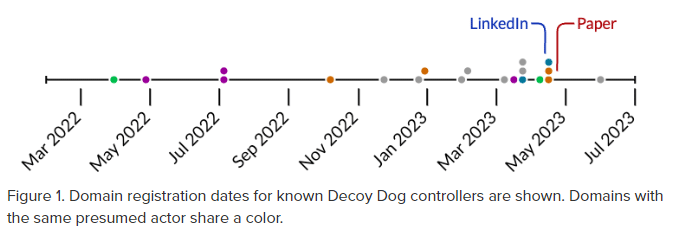
The initial sighting of the Decoy Dog controller was on cbox4.ignorelist[.]com, which became operational between late March and early April 2022. Subsequently, a second controller, claudfront.net, emerged in May 2022, displaying distinct characteristics that suggest a different threat actor may be operating it.
In July 2022, a third controller domain, allowlisted.net, was registered, strategically aged, and only became active in September 2022. This domain shares numerous similarities with claudfront[.]net, indicating a likely connection to the same actor.
Two additional controllers, hsps.cc and ads-tm-glb.click, were later established with unique attributes, signaling the involvement of a third threat actor using Decoy Dog.
It is worth noting that Infoblox is actively monitoring several other Decoy Dog domains beyond the ones mentioned above, and these may be associated with additional threat actors.
Over the past six months, there has been a consistent increase in domain registrations used as Decoy Dog controllers, with some registrations occurring immediately following Infoblox’s initial disclosure on LinkedIn.
Many aspects of Decoy Dog remain a mystery, but all signs point to nation-state hackers. Infoblox also released a new data set containing DNS traffic captured from Infoblox’s servers to support further industry investigation of the C2 systems.
The question many in the industry continue to silently ask is: Are we really securing our network if we’re not monitoring our DNS?
There is a significant risk that Decoy Dog and its use will continue to grow and impact organizsations globally. Currently, the only known means to detect and defend against Decoy Dog/Pupy today is with DNS Detection and Response systems like Infoblox’s BloxOne® Threat Defense.
“It’s intuitive that DNS should be the first line of defense for organizations to detect and mitigate threats like Decoy Dog. Infoblox is the industry’s best-of-breed DNS Detection and Response solution, providing companies with a turn-key defense that other XDR solutions would miss,” said Scott Harrell, Infoblox President and CEO.
“As demonstrated with Decoy Dog, studying and deeply understanding the attacker’s tactics and techniques allows us to block threats before they are even known as malware.”
Through large-scale DNS analysis, Infoblox has learned key features of the malware and the actors who operate it. Directly following the first announcement on social media, every Decoy Dog threat actor responded to Infoblox’s disclosures in different ways.
Some of the name servers mentioned in Infoblox’s April 2023 report were taken down, while others migrated their victims to new servers. Despite their efforts to hide, Infoblox has continued to track the activities and has since learned a great deal more about them.
Infoblox has been able to infer the nature of some communications, and estimates that the number of compromised devices is relatively small.
Additionally, Infoblox has also been able to distinguish Decoy Dog from Pupy and determine that Decoy Dog has a full suite of powerful, previously unknown capabilities, including the ability to move victims to another controller, allowing them to maintain communication with compromised machines and remain hidden for long periods of time. Some victims have actively communicated with a Decoy Dog server for over a year.
“The best defense against this malware is DNS,”
Dr. Renée Burton
“The lack of insight into underlying victim systems and vulnerabilities being exploited makes Decoy Dog an ongoing and serious threat,” said Dr. Renée Burton, Head of Threat Intelligence at Infoblox.
According to Dr Burton malicious activity often goes unnoticed because DNS is undervalued as a critical component in the security ecosystem.

“Only enterprises with a strong protective DNS strategy can protect themselves from these types of hidden threats.” Dr Burton said.
Currently, Infoblox oversees the monitoring of 20 Decoy Dog domains. Among them, several were registered and deployed in the past month.
The toolkit takes also advantage of a fundamental vulnerability within the prevailing malware-centric intelligence ecosystem, which largely governs the security industry today. Remarkably, the discovery of this malware was made possible solely through the application of DNS threat detection algorithms
Organisations best defense against these attacks is protection at the DNS level, within every network. Infoblox’s BloxOne® Threat Defense customers remain protected from Decoy Dog and these known malicious threat actors.







