What is Active Directory?
Active Directory is the central repository of information for Microsoft Windows based servers. Active Directory is designed to support access management and security features that are common with most modern corporate environments. Active Directory can be thought of as an internet directory. Users access this directory via Active Directory permissions, which are set on objects in Active Directory. The objects themselves are managed by security features in the Active Directory server.
Active Directory stores data in objects. An object is simply a single entity, like a user, group or program. Organisational objects are commonly defined as computers or other hardware and software, or security principals, like users or groups. The Microsoft Windows Server stores domain information in Active Directory and it allows users to manage it just like they manage any other type of computer data.
Active Directory also stores domain user access permissions. Permissions allow users to gain access to certain portions of a domain. This is one way Microsoft helps maintain security on their networks. Permissions can also be set to allow or deny access to shared folders and other objects within the Active Directory hierarchy.
Active Directory also enables Microsoft to track all of a person’s computer activities. This includes running processes and accessing files and other network resources. Active Directory is designed to help Microsoft keep track of user activity and to assist with network maintenance. By using an Active Directory interface, a computer user can gain access to their own computer information and to other computers that are specified by Microsoft in its Active Directory network.
Active Directory also includes a feature known as Active Directory management. This feature manages the usage of special permissions, access control permissions, and other types of access control lists. This feature makes it easier to administer networks. Special permissions can include Read/Write, Execute, and Create and modify permissions.
An important role that Active Directory plays in Microsoft Windows is the implementation of NFSv4. NFSv4 is the newer version of the Network File System, better known as NTFS. NFS is used to allow computers to connect to each other over large distances without having to use connection files, and is largely responsible for the growth of the Active Directory service. NFSv4 is similar to other types of file systems such as FAT and FAT32, but has some additional capabilities that Microsoft has deemed necessary for their networking applications.
Active Directory was developed as an extensible association directory that stores network settings and associated information in a hierarchical fashion. The advantage of using this design is that the user can easily gain access to all the settings that apply to all the domains of the Active Directory structure. On the other hand, if one were to work with only one domain, it would be much easier to work with. In addition to the standard Microsoft Active Directory servers, there are also third-party Active Directory server implementations available that can store and manage domain information more efficiently than Microsoft’s versions. Although Microsoft provides the bulk of Active Directory functionality, third-party vendors have provided a number of different add-ons that make working with the service easier and more efficient.
The two types of permissions commonly found in Microsoft Active Directory are the security descriptors and the permission lists. The security descriptors are per-user and per-group, while the permission lists are per computer and per registry. Permission lists are essentially a list of options that a user may choose when creating a security context, which allows the machine to automatically assign permissions to objects when they are created or modified. An example of a security dictionary would be Windows Security Settings, which might include settings such as “allow local users to connect to Microsoft Exchange.” Permissions are essentially a list of options, which only allows specific objects to be accessed or modified. Security descriptors are essentially a series of rules that allow a user to grant or deny a particular permission, while a security dictionary grants or denies permissions on a per-user or per-group level.
Active Directory Security
Active Directory Security is a very important part of a company’s Active Directory setup. The importance of this setting cannot be underestimated. The fact of the matter is that when you do not have an Active Directory security policy, you are opening your company up to all kinds of risks and dangers. If you are an administrator or a server administrator, it is imperative that you know about the various types of threats that are faced by your company, and then you must be able to implement solutions that will protect your company from these threats.
How Active Directory can be compromised
There are three main ways that Active Directory Security can be compromised: Active Directory Users, Computers, and Computers in a Directory. In the context of the Active Directory Users in a Directory, this implies that there are objects in your company’s Active Directory that are users in your company’s directory. These Active Directory users normally have Read and Write permissions on these objects. Most administrators think that these objects are safe because they are not stored locally on their computers, but things are not always as simple as that. If a hacker is able to get a hold of your company’s Active Directory, he or she may be able to access the files that these users have access to by using “iddler” scripts. This means that these users are only able to read and write files that are within the scope of their Active Directory Installation.
Directory Replication
Active Directory replication is when you have two separate copies of your Active Directory database on different computers, one on each LAN or WAN connection. Although this may sound very complicated, it is still doable in some companies, especially if your company’s LAN is quite wide. What happens here is that Active Directory data is copied across multiple locations, and because of the difference in the location of the servers, there are great differences in directory information between the Replicated Sites and the main Active Directory site.
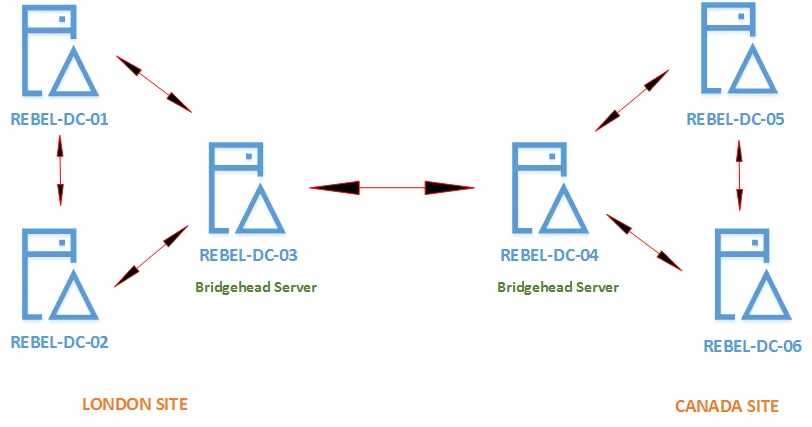
Active Directory Objects
An Active Directory security risk is also when network users gain access to the Active Directory objects on another system. If they have correct administrator privileges, they can gain access to all the objects, regardless of whether they are on the primary or the replica site. If a network user gets the correct access rights to the Active Directory objects, then he or she can then edit, add, or remove entries from this directory data. However, what happens when these people do not have the correct authorisation? A security vulnerability in Active Directory replication occurs when network users to gain administrator access to the Replicated Sites, and they have the ability to change the content of the directory data that was originally on the primary site. If any changes are made to this data on the Replicated Site without proper authorisation, then it can result in severe consequences for the primary site, because the security of the data is no longer assured.
When an employee logs on to an Online ID, it is not always his or her computer that is logging in. An employee can log onto any number of computers that are connected to the Active Directory system. Because of this, it is possible for a person to connect to an Active Directory system with unauthorised access, using a variety of devices, including Kerbaceous Earth devices, thumb drives, pens, and other devices that are capable of carrying out denial-of-service attacks against the servers. Such attacks make it difficult or impossible for network administrators to determine who has accessed particular Active Directory objects and what action is required.
Active Directory security issues can be particularly serious if data is stored in a way that makes it easy for even unauthorised users to gain access to it. One common mistake that organizations make is storing Active Directory data in the same place where it is commonly used. For example, Active Directory databases are commonly stored on network storage disks such as CD-ROMs and other data capture devices. It is also common for organisations to store their Active Directory information in a directory on their network servers, which is another piece of server equipment that is commonly used. With all of these pieces of Active Directory equipment in place, it is easy for an unauthorized user to gain access to any of the information that is contained within Active Directory.
Group Policy Objects.
A GPO, or Group Policy Object, is an extremely useful computer tool that allows you to centrally manage your company’s computers. The primary benefit of having a GPO is you can centrally configure a multitude of servers or clients centrally from among several policy objects. A GPO consists of two main sections: Computer settings and user settings. Computer settings refer to the options that control the way the operating system will operate with your applications and services; these include things like the time and mode of login and other security options. User settings are what control how the computer will actually use the configured policies; for example, a User setting may allow or disallow the use of certain programs and features on a server.
Policy objects are groups of related selections that can be applied to specific computers or organisational units. Policy objects can include anything from software, operating systems, hardware, and so on. When a policy is applied to an organisational unit, it controls the execution of that policy across all of the computers in the organisation. Computers and other devices are isolated from each other; so when one computer is affected by a policy change, it does not affect or break any other computers. Policy changes can only affect each individual computer per policy.
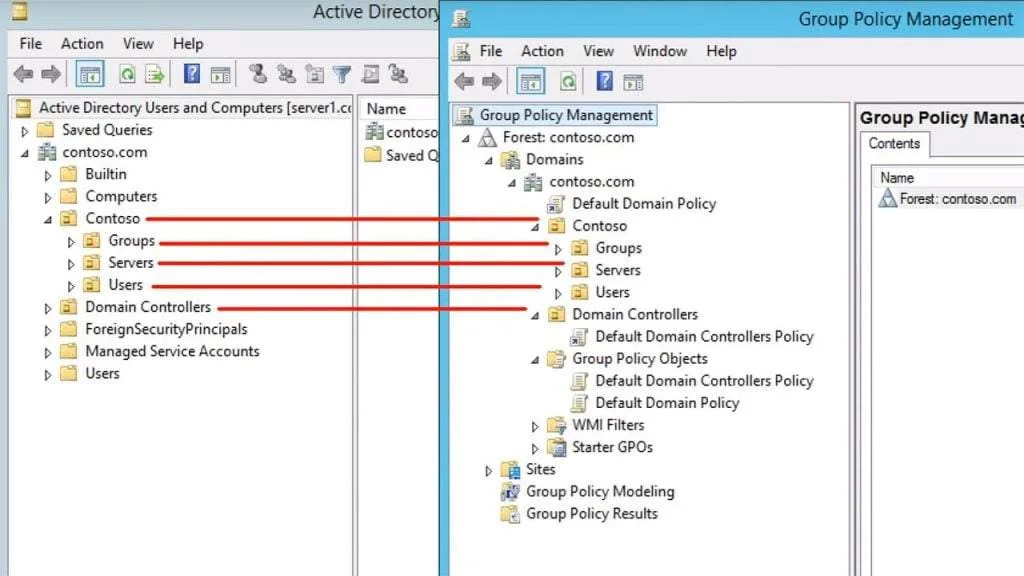
Domain Contollers.
In an Active Directory installation there are separate components involving Domain Controllers and zones. Domain controllers are Active Directory servers that allow users in the Active Directory to access their own account settings and associated data through an Active Directory VPN or Content Site. A domain controller can be single-point or multilayered and comes with various enhanced functions, such as dedicated IPsec and SSL certificates, security attributes such as Kerb count, password strength requirements, and more.
Active Directory security is enforced by policies and rules that are located on the domain controllers. Security is important in all environments and this holds true for an Active Directory as well. The following are the most important components of a domain controller and the security procedures associated with them:
These procedures will allow the administrator to enforce restrictions on the access to Active Directory objects, ensure that only authenticated users have access to objects, manage the distribution of security principals, configure access to registry keys, and enforce policy objectives. An enterprise will benefit greatly from having one unified infrastructure for their Active Directory maintenance activities and from one company single point of entry for all types of data. However, this brings with it certain challenges. One such challenge is that Active Directory security is very strict and needs to be strictly enforced. Changes to the infrastructure may cause some security violations by the Active Directory Users and this could have a serious impact on the business. For instance, changing the physical structure of the Active Directory site from one server to another within the same network could break this strict security policy and create problems for the Active Directory environment.
Domain Policy
When a user logs on to a computer in your company, his or her first interaction will be with the Default Domain Policy or the Default Password Policy. Once this has been applied, all further interaction with the computers will be controlled by this default password policy. This is a vital part of your network security and if it has not been applied or activated, you can be sure that every person who has access to your network is safe from any harm.
Securing Active Directory
It is important that all companies take the necessary steps to securing their Active Directory setup. Even the smallest businesses should take this step since it will allow them to protect their sensitive information from being stolen and used by unscrupulous people. But with so many security threats out there right now, there’s a lot that you can actually do to improve your Active Directory security. In this article, I’m going to show you 5 of the best practices you can apply to your company to make sure that your security is at its highest. Here they are:
Make sure that you’re not relying on too much built-in Active Directory features. While the built-in security that comes with your Windows Server might make it seem like a good idea, it is actually one of the biggest weaknesses when it comes to securing your Active Directory setup. If you have security that relies on too many Active Directory objects, then you are significantly more vulnerable to security threats than you might realise.