VPN stands for Virtual Private Network. In simple to use, the word generally indicates one of the following things:
- A service which makes use of a VPN tunneling technology.
- A networking device which enables you to create a private network within your own computer.
- A program or tool that helps you browse the Internet while keeping your identity secret.
The concept of VPN is fairly easy. You can make use of IP changing servers (an application) to hide your identity while connecting to the internet. Your location becomes hidden, and only your IP address is visible to other users. This concept of a virtual private network has gained much popularity recently among users who are in need of secure internet access.
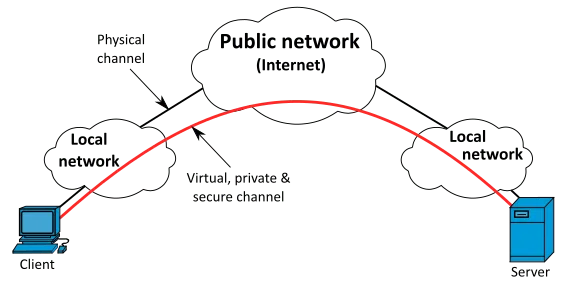
Private VPN is different from normal public networks, in that there is no physical server. The VPN server(s) provide an interface between your computer(s) and the IP network.
You may think that private VPN is a great solution for those who wish to surf anonymously, but this is not entirely true. While there are some ways to surf anonymously through a VPN, particularly when surfing through sites that do not offer a proxy option, it is possible for you to become completely anonymous if you purchase a virtual private network card and use it with your computer(s).
As you may have guessed, a VPN service offers better security when it comes to sensitive data. Any connection made through a VPN offers protection against unauthorised access. This is achieved through the installation of a special type of hardware that allows network infrastructure to be placed between you and the remote access server.
Since your network infrastructure consists of a set of devices that each have their own private connection to the internet, there are fewer or no connections available if someone were to attempt to gain access to these ports.
Not all businesses or organisations use vpn services to protect intellectual property. They do this because they have more serious concerns that a standard network infrastructure would not be able to provide.
For instance, in the finance industry, sensitive client information often travels between different offices. A standard network infrastructure would break down these communications, causing the client to lose control of their account. VPN technology solves this problem.
VPN Security
Not only does a VPN service offer protection against unauthorised access, it also protects against security threats. Public VPN connections are susceptible to attack from other users on the internet; especially if the public VPN goes down. Secured VPN connections use advanced protocols and different encryption methods that provide greater security.
The security benefits of VPNs go beyond protecting company information, confidential client information, and financial data. Certain types of online activities, such as certain forms of gaming, require the use of a form of encryption tunnel that prevent detection from outside parties. An encrypted VPN can make it impossible for a hacker to intercept or trace any of the user’s activities online.
Some open networks feature private tunneling capabilities that allow users to securely connect to the public internet without exposing sensitive information or going through security vulnerabilities.
These private VPN connections are not always available, however. Many businesses and institutions that rely on a variety of shared internet connections for their IT systems do not have this option.
The cost of setting up a VPN connection could also prove expensive. However, it is important to consider all of the available options before choosing the correct VPN for your organisation’s needs.
VPN Clients
Cisco Systems AnyConnect VPN Client is an easy-to-use software application for establishing secure VPN connections to virtual private network systems (Virtually everywhere in the world) using any one of hundreds of compliant gateways.
With a VPN, you can establish VPN connections between two remote locations through two independent networks – on the one hand, and between two internal systems on the other. You can use a VPN to prevent unauthorized access to your network from the public Internet or to protect sensitive data and applications from being compromised in a cyber attack.
When a VPN client is installed between two end-points, it creates a private tunnel for the purpose of transporting sensitive data and communications between the client and server. This connection can be either tunnels created within the client system itself or external connection using a VPN server. A VPN client serves as an interface between the VPN server and the client system.
The following is a brief introduction on how VPN clients
1. VPN Clients uses different sets of VPN protocols for enabling secure VPN connections. Some of the popular VPN protocols used are Diffie-Calibration, Secure Socket Layer (SSL), and OpenSSL
These VPN protocols secure the VPN traffic as much as possible by encrypting sensitive information and securing the data transport over the internet. The most common approach used in designing and deploying VPN clients is to create VPN connections over the public network such as the internet or a local intranet.
2. A VPN client can connect to an IP address. It uses this IP address during the initial VPN connection request to the VPN provider. Upon successful connection, the client will establish a secure session with the VPN provider where they will negotiate the important details of the key exchange process.
Once these are successfully negotiated, the client will be granted permission to create a VPN connection. Once the negotiation is completed, the VPN client will be able to access the network that they want to access.
3. Many companies and organisations today use an open source VPN client to maintain optimal security and functionality at all times. An open VPN client provides a highly flexible connection option to the consumer.
Open VPN clients allow configuration of the security settings to match corporate needs. They also provide the flexibility to configure gateway services and even firewall services. Most importantly, an open VPN client is not tied to any particular provider or network connection.
There are two different categories of VPN Clients. They are – PPTP VPN Clients which is the most widely used VPN clients; while NCP secure VPN Clients is preferred for business and enterprise networks.
In order to get started with the most suitable VPN Clients for your organization or business, it is recommended to contact a reliable NCP provider. NCP providers provide you with expert guidance on the most suitable configuration for your organisation or business.
VPN Servers
VPN Servers are the backbone of VPN, or Virtual Private Networking. A virtual private networking system allows users to send and get data over a public or shared network as if their computer systems were actually connected directly to the internal network..
The original VPN has become much more popular over the years due to its use for both private and commercial VPN solutions
There are many different types of VPN Servers available to connect to a VPN network. The two most common, and the most efficient, are IP-based (IP-based VPN) and tunneled protocols.
With an IP-based VPN, users can access VPN servers with their current Internet connection. Tunneled protocols, or VPN services, allow for connections to be established between VPN servers and Internet resources like email and web browsing.
IP-Based VPN
With the increasing popularity of VoIP, IP-based (which includes older ISDN), and cable/wireless providers, more businesses are finding that it is more practical to use an IP-based VPN rather than a traditional private network (PVC) – especially for their employees.
A private network has many advantages over an IP-based one, such as portability, flexibility, and reliability. However, even with these advantages, the cost of maintaining this type of network is much higher. So businesses may find it necessary to convert their current private networks to IP-based ones in order to save money.
An IP-based VPN, or virtual private network, allows users to connect through the Internet to resources that are located on another location. This type of hosting is called IP-based VPN, which stands for “IPvable Public Network.” Some typical IP-based VPNs include cabled and wireless connection options.
The primary advantage to this type of hosting is that it allows you to access the Internet using another network (outside of your own), without using a private network, which can be much more expensive. An IP-based VPN can be used for common applications like emailing, web browsing, and common internet telephony.
VPN Tunneling
VPN Tunneling is a method used to hide your identity and location through the use of a public network such as the internet. It can be likened to a virtual private network that makes you appear to be located at a different location than you really are in reality. The main advantage of this method is that it gives you access to the internet while keeping your identity hidden from anyone who might wish to misuse your personal data.
To understand how vpn tunnels work, you first need to know what exactly is a VPN and how it works. A VPN is also known as virtual private network. A VPN is used to secure your information such as credit card numbers, social security numbers and even telephone numbers so that when you connect to the internet, no one can view or control these sensitive details without your authorisation.
So how does vpn tunneling work? This method uses an encrypted connection through the internet to connect two or more end-points. The encrypted connection makes it impossible for anyone to eavesdrop on the information being sent or received and to read any of the information being passed.
This is done through the process of encryption, which makes it impossible for anyone to decipher the information being passed. The connection therefore goes between two servers and clients and is kept secret, which is only known at the very end – the point where both clients and servers to reach the end-point after connecting.
VPN Routers
VPN routers secure all your devices from each other, and it improves some benefits in saving money and time. VPN Ethernet router helps you in getting connected to the Internet with great speed, giving you the ease to access websites on the internet. VPN works by connecting you to a network of servers through a private network.
The VPN routers are available for both L2TP vpn and standard IP networking protocols. It is up to you which protocol to use. L2TP VPN routers provide complete protection of the system while allowing all your users to connect to the network as if they are local to you.
There are two types of VPN networking protocols – L2TP and IPsec (IPsec VPN). L2TP VPN uses a public key infrastructure (PKI) that is digitally signed on to the network. On the other hand, IPsec VPN uses a private network gateway (PGP) that authenticates the data packets between the VPN and the internet.
You need to consider all the pros and cons before purchasing a VPN router. You must be aware of the speed of connection as well as the type of firewall and filtering features that you might require while using the VPN. You should also check if the software installation process is easy and quick.
VPN Providers
For those who use the internet regularly, it is but obvious to use VPN or Virtual Private Network. VPN is an option which you can take to protect your privacy on the internet as well as for downloading web pages of large websites.
With a VPN, you can bypass the router and connect directly to a secure server. VPN also provides complete security to your websites and online activities.
The technology of VPN/wireless is getting popular with the passage of time because of its added features and ease of use. There are many providers of vpn services and each one has something unique to offer you.
Before choosing a VPN provider, it is important for you to know the benefits of using a VPN. If you want to know more about a specific VPN provider, then do a detailed search on the internet or visit a VPN review site.
In the reviews, you would get a clear idea about the quality and performance of the service provider. It is better to opt for a reputed VPN provider as it would ensure a higher level of performance. So, you should always look for a reputed vpn provider after going through the reviews.
Apart from the security, another major advantage of a VPN is that you can use various protocols while accessing internet via VPN. A common protocol used by users is encryption. Encryption is used so that the data, whether personal or confidential, is not accessed by anyone else apart from the intended user.
Most of the free VPN services offer encryption protocols and hence provide excellent protection to your network. A good VPN provider would always offer you a free VPN service, which helps you to test the compatibility and usability of the software before buying a service.
List of VPN Providers
- ExpressVPN
- NordVPN
- Hotspot Shield
- Surfshark
- CyberGhost
- ProtonVPN
- Norton Secure VPN
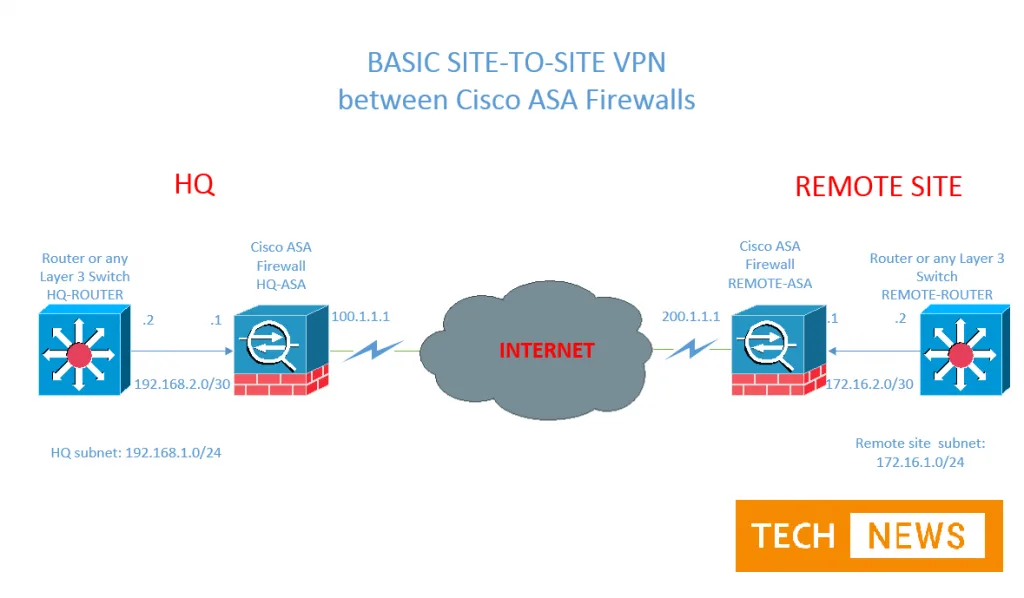
Site to site VPN
Site to site VPN is an internet connectivity method that ensures secure and fast exchanging of data between two or more locations through the use of internet connection.
Site to site VPN uses a high-speed or broadband connection via modem, network card or wireless device and internet service provider (ISP). A site to site virtual private network (VPN) connects two or more end-user sites, which may be internally or externally connected.
This is an excellent choice for companies that need to maintain separate infrastructure for different internal users from the corporate. For example, it may allow the company’s IT professionals to access their email system from a laptop in the field office.
Site to site VPN is usually used in tandem with branch offices in the case of multiple locations where employees are based. The VPN enables them to have access to information from other branch offices even if they are not located at the main office.
Branch offices can also use the VPN technology to establish secure back-up connections whenever they want to connect to the internet from another location, and this will ensure that the employees’ privacy is maintained at all times.
The major advantage of using a Site to Site VPN technology is that it offers secure connectivity between end-user locations even when the end-users are not connected to the local area network or the internet through their own internal wireless devices or a wired modem.
Most of the businesses today are now moving towards managed VPN services as they provide better flexibility, scalability and cost savings. Virtual private servers are ideally used for offshore companies, branch offices, or some remote locations where privacy and security are a concern. In most cases, such VPS solutions are able to maintain the privacy and security of the business data.
Managed VPN Services
A VPN is often used with managed VPN services to secure sensitive data. While a VPN is part of managed SD-LAN services to safely connect multiple remote branches to your enterprise network, you may wish to utilise a managed VPN independent from SD-LAN to connect multiple remote workers to your company’s internal network.
Using this kind of VPN will help several remote workers securely connect to your company’s internal network from virtually any location, anytime.
To do this, one requires a secure VPN connection that is not affected by the type of Internet connection used by the users. Most importantly, make sure the VPN server used does not share any bandwidth with other servers for your organisation.
To utilise managed VPN services, a user would require a suitable connection to the internet from within the corporate structure. For instance, if there are employees working from different departments at the same time, then a workgroup VPN or workgroup network would be a suitable option.
VPNs can also be used to protect against hackers by changing the IP of the user’s computer and make it appear that he is located at another location. To get the best advantages of managed lens solutions, it is important to find a provider with extensive experience in the field and offers multiple VPN solutions that can be tailored to meet your business needs.
Protecting your Business
Using a VPN to protect your business from Internet threats is vital. A virtual private network gives you complete security from malicious network attackers while maintaining easy Internet access for all employees.
As a business owner, you can enjoy a number of advantages that only a VPN service can offer. By establishing a VPN, you can keep track of employees who are accessing your site or are in charge of customer service.
You can also check the availability of support services and manage tickets remotely. If you need to know if there are any problems with a customer service call, you can simply connect to the VPN and make sure that your customers are satisfied.
As a business owner, you may want to protect your sensitive data or intellectual property. A VPN service offers excellent protection against hackers and others that would try to misuse or copy your data.
You can also set up a VPN server that works just like your business computer in order to maintain privacy and anonymity when you are on the web. The fact that you are connected through a secure VPN makes it easy for you to browse the Internet. In addition, a VPN service will allow you to make changes to your website that are otherwise not possible.







