The prevalence and sophistication of cyber threats have escalated, posing significant risks to individuals, businesses, and governments. Understanding these threats is the first step towards developing robust cybersecurity measures.
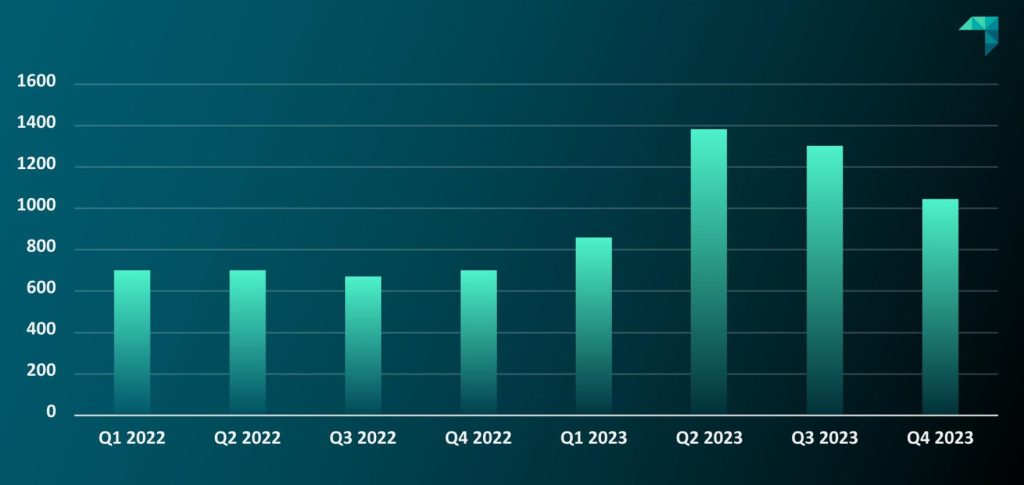
There is no doubt that 2023 was a challenging year for cybersecurity. The number of data breaches continued to increase, building on already alarming levels from previous years.
Additionally, there was an exponential rise in the complexity and intensity of cyberattacks, including social engineering, ransomware, and DDoS attacks, largely facilitated by hackers leveraging AI tools.
In recent years, the cost of breaches has steadily risen. The shift to remote work opened new security vulnerabilities, expanding the attack surface that hackers can exploit from their home offices.
The widespread presence of malware and hackers across all commercial sectors has increased the susceptibility of everyone connected to the internet to breaches.
With numerous criminal adversaries and countless entry points, effective containment and mitigation are exceedingly difficult. Unfortunately, cyber statistics are expected to remain alarming in 2024.
According to Crowdstrike.com identity threats exploded in 2023. Adversaries, including groups like SCATTERED SPIDER, have begun leveraging generative AI to enhance their infiltration methods.
These methods now include phishing, social engineering, and purchasing legitimate credentials from access brokers. Additionally, tactics such as SIM-swapping, bypassing multi-factor authentication (MFA), and utilising stolen API keys for initial access have gained popularity.
Adversaries are escalating their tactics at an alarming rate. In 2023, the average eCrime breakout time — the interval for an adversary to move from an initially compromised host to another within the organisation — was reduced to just 62 minutes, compared to 84 minutes in the previous year. The fastest recorded breakout time was a mere 2 minutes and 7 seconds.
Human intervention is a significant factor in the majority of today’s attacks. In 2023, interactive intrusions increased by 60%, with 75% of initial access attacks being malware-free.
Adversaries are shifting away from traditional malware and malicious attachments, opting for more covert and effective methods like credential phishing, password spraying, and social engineering.
With stolen identities, adversaries can log in using legitimate credentials, which has become one of the fastest and most common methods of gaining access.
List of Cyber Threats In 2024
1. Phishing Attacks
Phishing is a social engineering attack where attackers masquerade as trustworthy entities to steal sensitive information such as usernames, passwords, and credit card details. These attacks often come via email, with messages designed to trick recipients into clicking on malicious links or downloading infected attachments.
2. Malware
Malware, short for malicious software, encompasses various harmful software types, including viruses, worms, ransomware, spyware, and trojans. Malware can damage or disable computers, steal data, or allow unauthorized access to systems.
- Viruses attach themselves to legitimate files and spread across systems.
- Worms replicate themselves to spread to other computers.
- Ransomware encrypts a victim’s files and demands a ransom for the decryption key.
- Spyware secretly monitors and collects user information.
- Trojans disguise themselves as legitimate software to gain access to systems.
3. Ransomware
A particularly damaging type of malware, ransomware encrypts the victim’s data, rendering it inaccessible until a ransom is paid. High-profile incidents have targeted hospitals, schools, and businesses, often leading to significant financial losses and operational disruptions.
4. Denial-of-Service (DoS) Attacks
A DoS attack aims to make a computer, network, or service unavailable to its intended users by overwhelming it with a flood of internet traffic. Distributed Denial-of-Service (DDoS) attacks amplify this threat by using multiple compromised systems to generate the attack traffic, making it harder to defend against.
5. Man-in-the-Middle (MitM) Attacks
In a MitM attack, attackers intercept and potentially alter communication between two parties without their knowledge. This can happen through compromised Wi-Fi networks, where attackers can eavesdrop on or manipulate the data being exchanged.
6. SQL Injection
SQL injection is a code injection technique that exploits vulnerabilities in an application’s software. Attackers insert malicious SQL code into a query to manipulate the database, allowing them to access, modify, or delete data. Web applications that do not properly sanitize user input are particularly vulnerable to this type of attack.
7. Zero-Day Exploits
Zero-day exploits target vulnerabilities in software that are unknown to the vendor. Because the vendor is unaware of the vulnerability, there is no patch or fix available, leaving systems exposed to attack. These exploits are highly prized on the black market and can be used to execute a range of malicious activities.
8. Advanced Persistent Threats (APTs)
APTs are prolonged and targeted cyber attacks where an intruder gains access to a network and remains undetected for an extended period. These attacks typically aim to steal data rather than cause immediate damage, often targeting large organisations and government entities for espionage purposes.
9. Insider Threats
Not all cyber threats come from external sources. Insider threats involve employees, contractors, or other trusted individuals who intentionally or unintentionally cause harm. This can include data theft, sabotage, or leaking sensitive information. Insider threats are particularly challenging to detect and prevent because the individuals already have authorized access.
10. Cryptojacking
Cryptojacking involves unauthorized use of someone else’s computer to mine cryptocurrency. Cybercriminals achieve this by infecting computers with malware designed to perform the complex computations needed for mining. This can lead to decreased system performance and increased energy consumption.
11. IoT Attacks
The Internet of Things (IoT) refers to the network of physical devices connected to the internet. While IoT devices offer convenience and efficiency, they are often poorly secured, making them attractive targets for cybercriminals. Compromised IoT devices can be used to launch large-scale attacks or gain access to more critical network components.

The Financial Toll of Cybercrime
Cybercrime’s financial repercussions are staggering. In 2023, the global average cost of a data breach rose to $4.45 million, marking a 15% increase over three years. \
The United States remains the hardest hit, with the average cost of a breach reaching $5.09 million. Remote work has compounded these challenges, adding an average of $173,074 to the cost of breaches, reflecting the new vulnerabilities in hybrid work environments.
Ransomware: A Dominant Cyber Threat
Ransomware continues to dominate the cyber threat landscape. In 2023, 72.7% of organizations globally fell victim to ransomware attacks. The financial impact is severe, with the average cost of a ransomware attack reaching $4.54 million.
Despite the high costs, nearly half of the companies affected by ransomware now have policies to pay ransoms, a 13% increase from the previous year. However, paying the ransom does not guarantee data recovery; only 8% of businesses that pay the ransom recover all their data.
Phishing: The Leading Attack Vector
Phishing remains the most common method of cyberattack, accounting for 39.6% of all email threats. This technique is often the precursor to more severe breaches, with 94% of malware delivered via email.
Spear phishing, a more targeted form of phishing, has been used in 62% of phishing attacks, highlighting the sophisticated nature of these threats.
Industry-Specific Impacts
Certain industries face unique cyber threats:
- Healthcare: The healthcare sector has seen a 239% increase in large breaches involving hacking over the last four years, with the average breach costing nearly $11 million. Reconnaissance activities, where attackers scout for vulnerabilities, are the leading type of impact in healthcare cyber incidents.
- Manufacturing: This sector is the most targeted by cyber extortion campaigns, accounting for 20% of all such incidents globally. The deployment of backdoors is the most common hostile action, occurring in 28% of cases.
- Financial Services: Financial institutions are particularly vulnerable, with an average of 449,855 sensitive files exposed per breach. It takes these organizations an average of 233 days to detect and contain a breach, exposing them to prolonged risks.
- Education: Educational institutions are also heavily targeted, with ransomware attacks causing over $53 billion in downtime costs globally from 2018 to mid-2023.
The Rise of AI in Cyber Threats
The integration of artificial intelligence (AI) in cyber operations is a double-edged sword. While AI offers advanced defense mechanisms, it also empowers attackers.
85% of cybersecurity professionals attribute the rise in cyberattacks to the use of generative AI by bad actors. Concerns include undetectable phishing attacks and a general increase in the volume and velocity of attacks.
Geopolitical Influences
Geopolitical tensions significantly impact cybersecurity. The Russia-Ukraine conflict has heightened cyber threats globally, prompting 97% of organisations to report an increase in threats since the war began.
In response, 51% of organisations updated their business continuity and enterprise risk plans in 2023 to address these evolving challenges.
Cyber Threat Predictions for 2024
As we move further into 2024, the landscape of cyber threats in Australia is poised for significant changes driven by advancements in technology and geopolitical developments. Here’s a detailed look at what we can expect in the coming year.
1. Artificial Intelligence Abuse
Artificial Intelligence (AI) has become a double-edged sword. While businesses continue to adopt AI tools to enhance efficiency, cybercriminals are also harnessing its power for malicious purposes.
In 2024, AI is likely to automate aspects of cyber-threat campaigns, making attacks more scalable and reducing turnaround times. AI can enable threat actors to quickly write scripts and transition seamlessly between different operating systems, such as Windows, Linux, and macOS.
However, the use of AI by legitimate businesses might inadvertently expose private data, opening new avenues for cybercriminals to exploit.
2. Geopolitical Tensions and Hacktivism
Geopolitical developments will continue to influence the cyber threat landscape. Hacktivism is expected to remain steady or even increase, as political conflicts provide motivation for cyber attacks.
The “Cyber Toufan” hacktivist group, for instance, leaked data from Israeli companies in response to the Israel-Hamas conflict. Similar groups are likely to carry out destructive attacks in 2024, emulating the tactics of state-linked groups to further their political causes.
Pro-Russia hacktivist groups, such as “NoName057(16),” will likely continue supporting Russia’s interests amidst the ongoing Ukraine conflict, presenting a significant hacktivist threat in the coming year.
3. Enterprise Threats and Automation
Automation will play a critical role in cyber attacks in 2024. The exploitation of flaws, such as the Citrix Bleed vulnerability, and automated campaigns like Clop’s MOVEit attack, demonstrate how automation can expedite attacks through the kill chain, making them harder to detect and stop.
Phishing and business email compromise (BEC) are expected to remain prevalent. Additionally, SEO poisoning—a technique that uses legitimate SEO methods to push malicious websites to the top of search engine results—poses a growing threat.
The tactic, relatively unfamiliar to the general public, is likely to see a steady increase in use throughout the year.
4. Initial Access and Ransomware
Information-stealing malware (infostealers) will continue to be a primary method for gaining network access, especially for ransomware groups. Infostealers are often available as-a-service, making them accessible to less technically sophisticated attackers.
Malware loaders, such as “QakBot,” “SocGholish,” and “Raspberry Robin,” are expected to continue driving a majority of cyber-attacks. Although QakBot’s command-and-control infrastructure was disrupted by law enforcement, its operators remain at large and could resume activities in 2024.
Ransomware remains a persistent threat, with groups like “LockBit” leading the charge. LockBit, known for targeting banks, governments, and law firms, is anticipated to have another active year.
Extortion techniques are also likely to become more innovative, as cybercriminals seek new ways to pressure businesses into paying ransoms.
Cyber Threat Actors
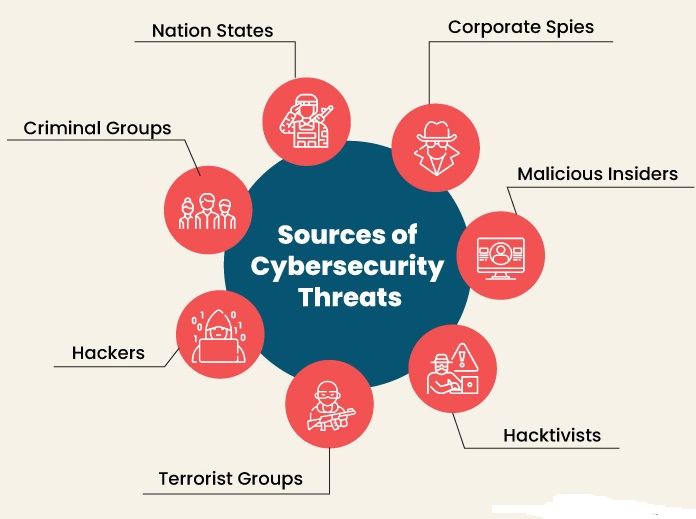
To respond effectively to cyberattacks, it’s imperative to know the threat actors and understand their tactics, techniques, and procedures.
- Common Threat Actors
- Nation States Cyber-attacks orchestrated by nations can severely disrupt communications, military operations, and everyday life.
- Criminal Groups These groups target systems or networks for financial gain, employing methods like phishing, spam, spyware, and malware to commit identity theft, online fraud, and extortion.
- Hackers Hackers use various techniques to breach defenses and exploit vulnerabilities in computer systems or networks. Their motivations range from personal gain and revenge to financial profit and political activism. They often develop new threats for the challenge or to gain recognition within the hacker community.
- Terrorist Groups Terrorists use cyber attacks to damage, infiltrate, or exploit critical infrastructure, posing threats to national security, military equipment, the economy, and public safety.
- Hacktivists Hacktivists conduct cyber-attacks to promote political causes rather than for financial gain. They target industries, organizations, or individuals who oppose their political beliefs and agendas.
- Malicious Insiders Nearly all IT leaders are concerned about insider threats. These threats come from employees, third-party vendors, contractors, or business associates who misuse their legitimate access to enterprise assets for financial or personal gain.
- Corporate Spies Corporate spies engage in industrial or business espionage to profit or disrupt competitors by attacking critical infrastructure, stealing trade secrets, and gaining unauthorised access.
Cyber Threat Summary
The cyber threat landscape is set to be shaped by the dual forces of technological advancements and geopolitical tensions. AI will be a key player, both for its efficiency-enhancing potential and its misuse by cybercriminals.
Hacktivism driven by political conflicts will persist, while automation will further complicate efforts to defend against cyber-attacks.
Infostealers, malware loaders, and ransomware will remain significant threats, with evolving tactics designed to maximize their impact. Organisations must stay vigilant and adaptive, employing robust cybersecurity measures to protect against these emerging threats.
In 2024 the major threats to businesses include deceptive phishing attacks, malicious software (malware), and ransomware that encrypts files and demands a ransom for their release.
By being aware of these threats, individuals and organiaations can take proactive measures to enhance their cybersecurity posture, protect sensitive information, and mitigate potential risks.







