Configuration files are a great resource for maintaining a website with ease, but they are also a common resource for malicious actors.
Developers and website operators benefit from configuration files by avoiding the need to hard code or manually enter connection details, which would otherwise be required in a world without configuration files.
It would be cumbersome to find exactly where configuration details are kept, and to update all instances of reusable data. There would also be code bloat and possible performance issues. Even just changing a website would be a difficult task.
Configuration Backup Probing
Wordfence has detected 70,408,576 attempts to locate wp-config.php file backups in the last 30 days. This is so common that Wordfence’s firewall detected it.
For instance, the search phrase inurl:wp-config.php intext:DB_PASSWORD will return results for files containing wp-config.php within the URL that also contain DB_PASSWORD in the body of the file that loads.
Malicious actors often use scripts and prebuilt tools to automate the process of finding backup configuration files. Using some form of automation to find these files makes the process much more efficient.
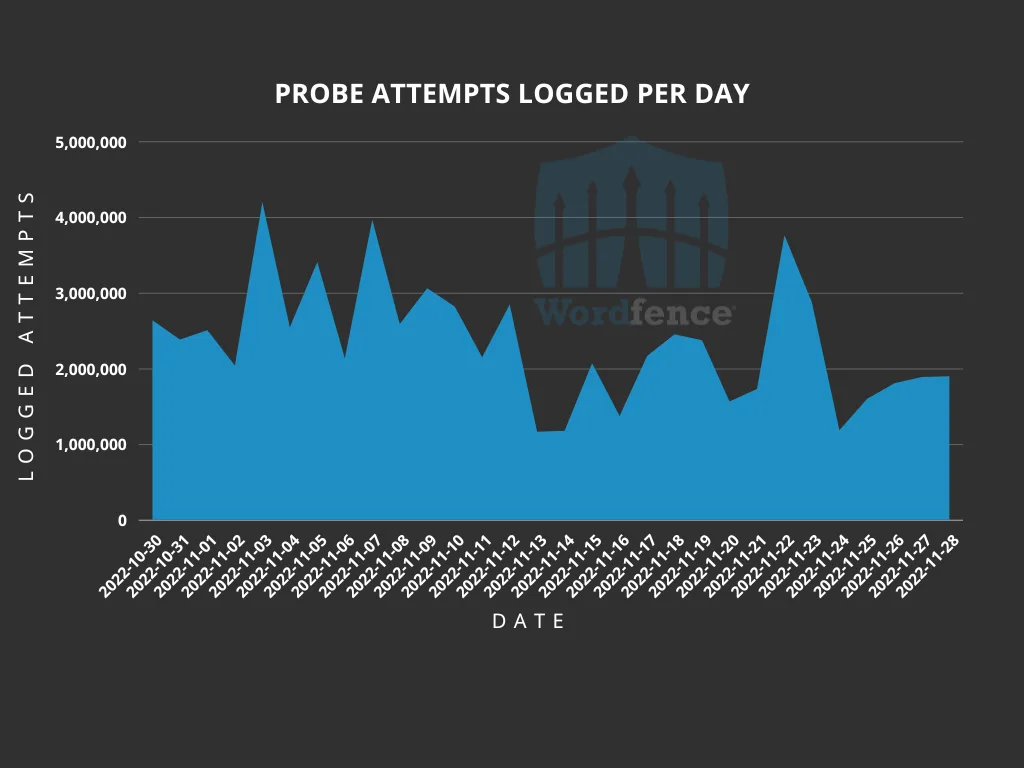
Wordfence found four legitimate uptime scanners that were detecting this file in this data. The issue with these scanners is that they are inexpensive and two of them offer free versions.
There is no justifiable reason to scan for wp-config.php backups, so malicious actors have concluded that the resources required to use these scanners are outweighed by the advantages of using a recognised legitimate solution for nefarious purposes.
A little over 6.5 million wp-config.php file backups are located using these scanners.
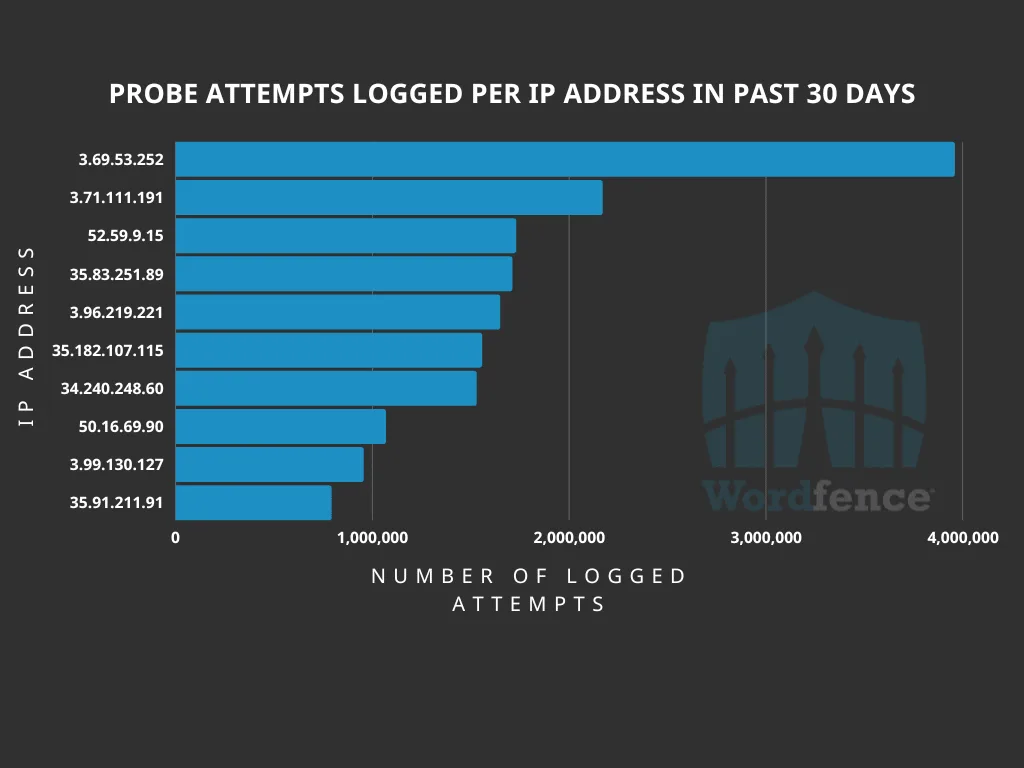
Here are the top ten IP addresses wordfence have blocked from probing for wp-config.php backups.
- 3.69.53.252 with 3953193 attempts
- 3.71.111.191 with 2165519 attempts
- 52.59.9.15 with 1726745 attempts
- 35.83.251.89 with 1707670 attempts
- 3.96.219.221 with 1645568 attempts
- 35.182.107.115 with 1553854 attempts
- 34.240.248.60 with 1526032 attempts
- 50.16.69.90 with 1065868 attempts
- 3.99.130.127 with 952639 attempts
- 35.91.211.91 with 789722 attempts
All of these servers are registered to Amazon and located throughout the world.
It’s common for threat actors to use servers in any location that could be useful to them, especially if there is a location that is known for allowing (or at least turning a blind eye to) the type of activity they will be using the server for.
Common Backup Mistakes
Making a backup of the wp-config.php file by making a copy and appending a new file extension like .txt, .bak, or .html is a common method. It’s a fast way to back up the file, and it can be restored by changing the filename back to its original.
The issue is that these files are available on the web, making it relatively easy for malicious actors to locate the sensitive information.
Extended Summary
Looking at the data gathered over the last 30 days, it is obvious that searching for configuration files such as wp-config.php is common among malicious actors. The database credentials alone can be very important to anyone wishing to seize a website.
Someone looking to take over a website might find wp-config.php files even more valuable than before, as over 40% of websites currently run WordPress (Barnes, 2018). This CMS only requires knowledge of one CMS to find wp-config.php files (Barnes, 2018).
The Wordfence Scanner includes an option to “Scan for publicly accessible configuration, backup, or log files”, which will notify you if any publicly accessible configuration, backup, or log files are present in your site’s directory.
For regular scans, this option is turned on, and you may check it for custom scans as well. If you discovered that you have a sensitive file that is publicly accessible, Wordfence strongly advise removing it immediately.







