Attackers have tested an exploit for a critical Office vulnerability already fixed by Microsoft.
In September 2021, Microsoft released a patch to prevent attackers from launching malicious code embedded in a Word document that downloads a Microsoft Cabinet (CAB) archive, which in turn contains a malicious executable file.
Sophos research found that the attackers reworked the original exploit by placing a malicious Word document in a specially crafted RAR archive. A new form of “no CAB” exploit attempts to bypass the original patch.
Researchers at global security company Sophos said this could indicate that a new exploit that was sent using spam for 36 hours could be reinstated at a later stage.
The original exploit affected the Office file format. To exploit this vulnerability, attackers could execute malicious code embedded in a Word document that downloads a Microsoft Cabinet archive that in turn contained a malicious executable file.
Sophos’s statement says: “The attackers rewritten the original exploit by placing a malicious Word document in a specially crafted RAR archive. A newer, “CAB-free” form of the exploit effectively bypasses the original patch.
“Sophos data shows that the amended exploit was used in the wild for around 36 hours.”
The research showed the limited lifespan of the updated attack could mean it is a “dry run” that could come back in future incidents.
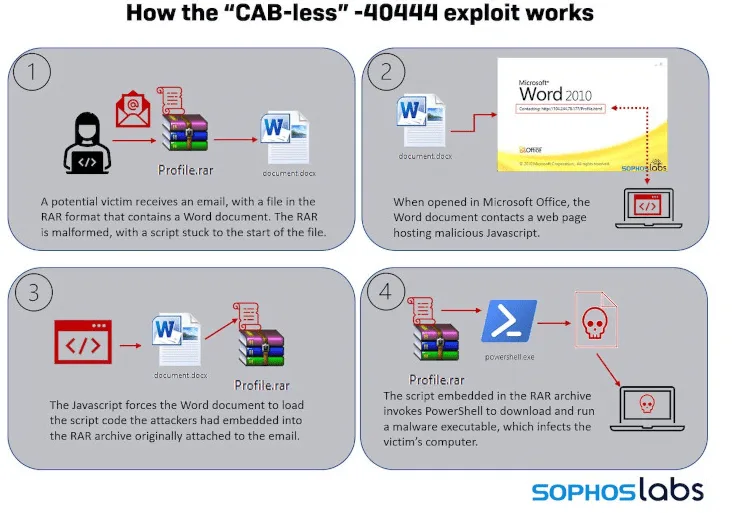
The pre-patch versions of the attack involved malicious code packaged into a Microsoft Cabinet file. When Microsoft’s patch closed that loophole, attackers discovered a proof-of-concept that showed how you could bundle the malware into a different compressed file format, a RAR archive.
RAR archives have been used before to distribute malicious code, but the process used here was unusually complicated.
It likely succeeded only because the patch’s remit was very narrowly defined and because the WinRAR program that users need to open the RAR is very fault tolerant and doesn’t appear to mind if the archive is malformed, for example, because it’s been tampered with.”
The Infection Chain
Sophos researchers found that the attackers had created a rogue RAR archive that had a PowerShell script prepending a malicious Word document stored within the archive.
The attackers created and distributed spam emails that included the invalid RAR file as an attachment. The emails were inviting recipients to unzip the RAR file to access the Word document.
Opening the Word document triggered a process that, on unpatched systems, ran the front-end script, eventually leading to an infection with the Formbook malware.
This study is a reminder that patching alone cannot protect against all vulnerabilities in all cases.
Setting restrictions that prevent a user from accidentally activating a malicious document can help protect against such exploits, but people can still be tricked into clicking the “Enable Content” button.
It is therefore vital to educate employees and remind them to be wary of documents sent by email, especially when they arrive in unusual or unfamiliar compressed file formats from people or companies they do not know. If in doubt, always check with the sender or someone in IT