The Wordfence Incident Response Team has reported an increase in infected websites hosted on GoDaddy’s Managed WordPress Service, which includes MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress sites.
These vulnerable sites have an almost identical backdoor added to the top of the wp-config.php file. Of the 298 sites that were infected with this backdoor five days ago on March 11, at least 281 are hosted on GoDaddy.
These affected sites have an almost identical backdoor attached to the wp-config.php file.
Of the 298 websites that were recently infected by this backdoor as of 5 days ago as of March 11, at least 281 are hosted on GoDaddy.
The incident response team started seeing an overall increase in infected sites starting on March 11th:
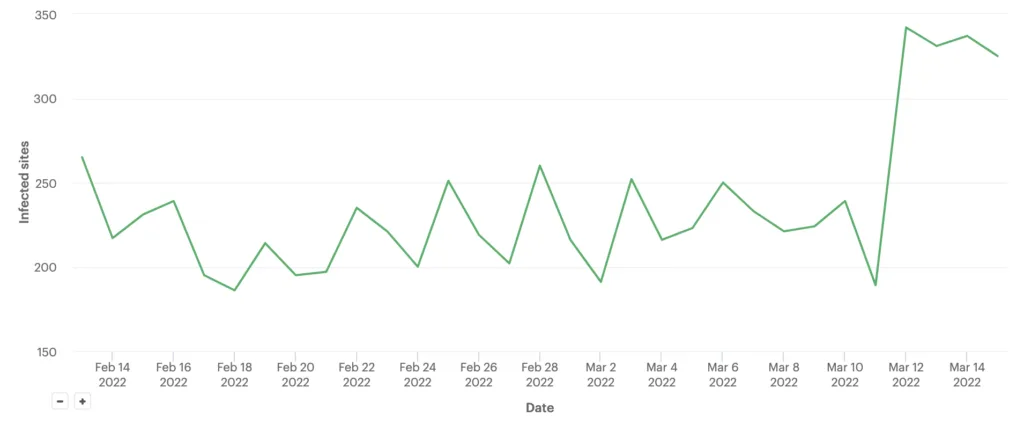
Managed hosting plans with GoDaddy include security tools and 24 hour support. The company also provides Malware scans and updates.
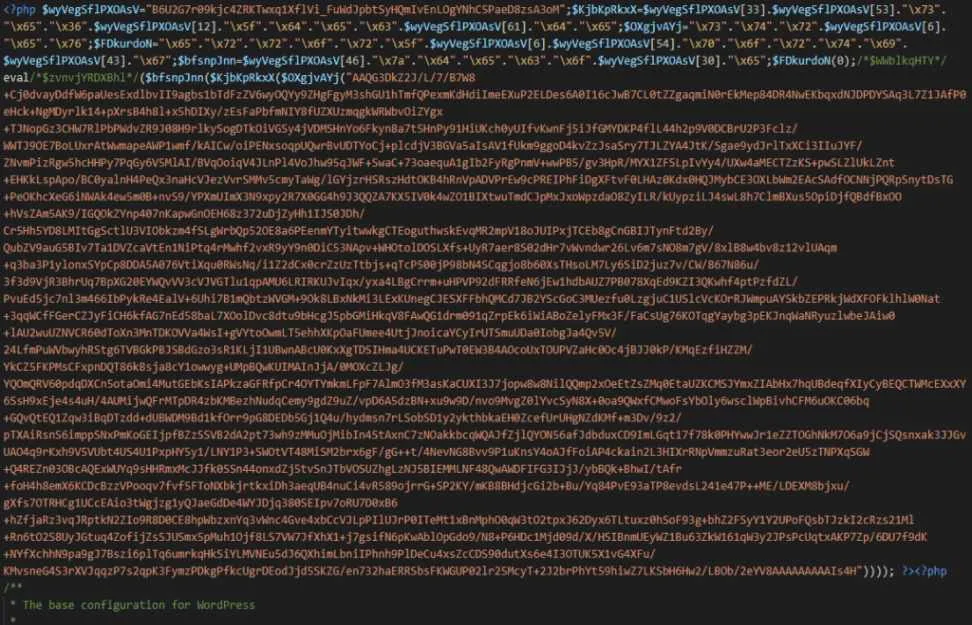
The backdoor in question has been in use since at least 2015. It generates spammy Google search results and includes features tailored to the infected website. The main backdoor is added at the beginning of wp-config.php and looks like this:
Wordfence said the have have not yet determined the Intrusion Vector for this campaign, but last year, GoDaddy disclosed that an unknown attacker had gained unauthorized access to the system used to provision the company’s Managed WordPress sites, impacting up to 1.2 million of their WordPress customers.
The WordPress security plugin provider also made a recommendation for website owners who have their website hosted on GoDaddy’s Managed WordPress platform (which includes MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress sites) to manually check site’s wp-config.php file, to make sure it’s not infected.
Wordfence made contact with GoDaddy security and have offered to share additional information with them. They did not provide a comment in time for publication.







