Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are malicious attempts to disrupt the normal operations of a targeted server, service, or network by overwhelming it with a flood of Internet traffic.
In general, DDoS attacks can be segregated by which layer of the Open Systems Interconnection (OSI) model they attack. They are most common at the Network (layer 3), Transport (Layer 4), Presentation (Layer 6) and Application (Layer 7) Layers.
The alarming acceleration underscores the growing sophistication and potency of cyber threats plaguing the digital landscape.
Findings also shed light on the evolving nature of cyber warfare, with geopolitical tensions serving as a catalyst for the surge in DDoS attacks.
The volatile global climate has provided fertile ground for malicious actors to exploit, with a notable uptick in attacks targeting critical infrastructure, public institutions, and political organisations.
Recent Example
In March 2023, during a fashion show in Melbourne, Victoria, a religiously motivated DDoS attack occurred following the display of a culturally offensive garment.
The attack was orchestrated by a dispersed hacktivist group spanning Pakistan, Indonesia, Malaysia, and Bangladesh. Their targets included various entities, from small organisations to prominent institutions such as educational establishments, banks, and government agencies.
Assaults driven by politically motivated groups, pose a significant threat
Of particular concern is the revelation that two thirds of observed DDoS traffic is machine-based, indicative of the widespread proliferation of bot activity. This proliferation underscores the need for robust cybersecurity measures to mitigate the impact of automated attacks and safeguard against potential disruptions.
Moreover, the report underscores the heightened security risk posed by vulnerabilities in web applications and APIs, exacerbated by the prevalence of unpatched software.
With the European Union’s recent mandate for Apple to open its interfaces to third-party providers, the urgency for enhanced security measures in this realm has been further underscored.
The emergence of AI-driven bots presents an additional layer of complexity to the cybersecurity landscape. Projections indicate a staggering 131% surge in online bot fraud by 2027, highlighting the pressing need for proactive measures to combat this evolving threat.
Development Of Attack Duration
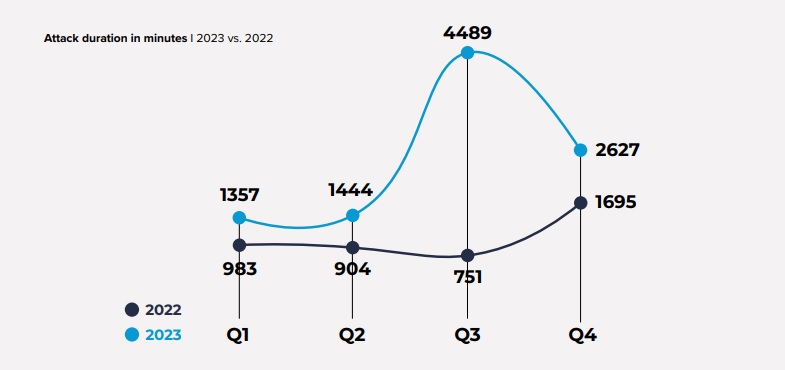
The duration of DDoS attacks observed in the Link11 network during 2023 exhibited a notable increase compared to the preceding year. An analysis of the provided chart reveals a distinct contrast in the duration of DDoS attacks between 2023 and 2022.
In particular, the longest attacks in 2023 were markedly different from those in the previous year. 2023 saw a prevalence of lengthier attacks, in stark contrast to 2022, where a trend towards shorter DDoS attacks was observed.
The most prolonged DDoS attack recorded in 2023 persisted for 4,489 minutes, equivalent to approximately 74 hours and 49 minutes. In contrast, the longest attack witnessed in 2022 lasted a significantly shorter duration, totaling 1,695 minutes or approximately 28 hours and 15 minutes.
Further examination reveals that the duration of DDoS assaults varied significantly, ranging from mere minutes to several hours. The majority of attacks (88%) lasted less than 5 minutes.
Approximately 5% of all documented attacks persisted between 5 and 10 minutes, while another 5% extended up to 60 minutes. A minority of attacks (2%) endured beyond the 60-minute mark. Notably, compared to the preceding year, the incidence of these prolonged attacks doubled.
The duration of a DDoS attack is intricately tied to the utilized attack methodology. Hackers frequently employ swift attacks targeting individual IP addresses to pinpoint vulnerabilities within the target’s IT infrastructure.
Conversely, rapid yet small-scale DDoS assaults often function as a smokescreen for concurrent hacker attacks directed at servers and networks. This tactic allows hackers to infiltrate undetected through secondary access points.
In response to such attacks, existing IT resources are rapidly mobilized to mitigate system failures and limit damage. Abruptly terminated short-duration attacks suggest that the attackers failed to breach their intended target.
In well-fortified infrastructures, attackers may retreat to conserve resources. However, in the case of sustained assaults, the objective is to inflict lasting disruption and harm upon the target.
Nevertheless, the duration alone does not signify the potency of a DDoS attack. Some attacks may peak without causing substantial damage, while others may wreak havoc, including complete service outage, before reaching their maximum potential.
Time-to-mitigate (TTM) assumes paramount importance, particularly for rapidly unfolding assaults. The Frost & Sullivan study titled “The New Benchmark: Why Fast DDoS Detection Is No Longer Good Enough” elucidates the efficacy of Link11 and other service providers concerning this critical metric.
Development Of The Attack Bandwidths
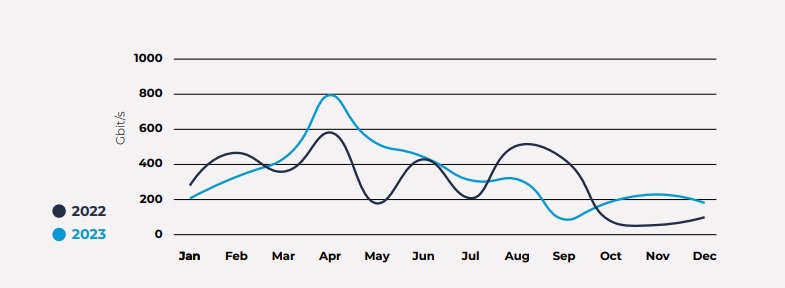
In 2023, there was a noticeable uptick in high-volume DDoS attacks compared to 2022. Throughout 2023, the bandwidth measured by the LSOC consistently surpassed the 100 Gbps threshold each month, as illustrated in the graph below.
Conversely, in 2022, there were substantial fluctuations, with bandwidth peaks in October and November falling well below 100 Gbps.
The most substantial attack recorded in 2023 reached 795 Gbps, marking a significant escalation from 2022’s peak of 574 Gbps. During the first half of 2023, high-volume attack bandwidths fluctuated between 261 Gbps and the highest single peak of 795 Gbps.
However, in the latter half of the year, the intensity of attacks subsided, with the largest DDoS attack in the third and fourth quarters capped at 303 Gbps.
The average total bandwidth surged from 2.6 Gbps in 2022 to 3.0 Gbps in 2023. This increase in intensity is evident not only in the higher average bandwidth but also in the volume of transmitted packets.
The period under review witnessed the highest packet rate ever recorded in the Link11 network, surpassing 168 million packets per second. Despite this, the average packet rate during this period stood at 625,000 packets per second, which was notably lower than the average in 2022.
The meticulous analysis of cyber threat data reveals a concerning trend: DDoS attacks are now reaching critical levels in a fraction of the time compared to previous years,
This alarming acceleration in DDoS attack intensity and frequency demands heightened vigilance and proactive measures from organizations and cybersecurity experts worldwide.
Strengthening cybersecurity frameworks, investing in advanced threat detection technologies, and fostering international cooperation are imperative steps in fortifying digital defenses and safeguarding against the growing menace of DDoS attacks.
Failure to address these vulnerabilities could have far-reaching consequences, underscoring the urgency for concerted action in the face of escalating cyber threats.







