As the industry grapples with a significant shortage of cyber security professionals, experts cautioning that the stakes have never been higher.
The surge in cybercrime threatens to undermine public trust in fundamental values such as democracy, capitalism, and personal privacy.
The nonprofit Information Security Forum, which positions itself as a leading authority on cyber and information security, highlights several critical risks in its annual Threat Horizon study:
- Disruption – An over-reliance on fragile connectivity raises the threat of deliberate internet outages that could cripple trade and increase the likelihood of ransomware attacks targeting the Internet of Things.
- Distortion – The intentional spread of misinformation, often propagated by bots and automated sources, erodes trust in the integrity of information.
- Deterioration – Rapid advancements in intelligent technologies, coupled with conflicting national security and privacy regulations, hinder organisations’ ability to manage their own data effectively.
According to a report from Cybersecurity Ventures, the cost of cybercrime skyrocketed to $8 trillion in 2023, averaging more than $250,000 every second.
The figure is projected to escalate to $10.5 trillion by 2025. Given these alarming statistics, it’s essential to explore the most pressing cybersecurity threats for 2024 and the strategies that can be implemented to mitigate them.
Types of Cybersecurity Threats
As digital landscapes continue to evolve, so too do the types of cyber threats that target them. These threats can be broadly categorized, each with its unique characteristics and methods:
- Malware remains a significant concern, encompassing various forms such as viruses, ransomware, and spyware. These malicious programs can disrupt operations, steal sensitive information, or damage systems.
- Social engineering tactics exploit human interactions to gain unauthorized access to valuable information and systems. Phishing, one of the most prevalent forms, tricks users into revealing confidential data.
- Insider threats originate from within an organization and can be either accidental or malicious. These threats are particularly insidious, as they often bypass traditional security measures due to legitimate access.
- Advanced persistent threats (APTs) represent complex and stealthy attacks aimed at specific targets, seeking to steal data or disrupt operations while remaining undetected for extended periods.
- Distributed denial of service (DDoS) attacks overwhelm systems with massive amounts of internet traffic, disrupting services and potentially serving as a smokescreen for more invasive attacks.
- Ransomware attacks involve encrypting the victim’s data and demanding payment for decryption keys, which can paralyze critical systems and lead to significant financial losses.
- Man-in-the-middle (MitM) attacks intercept communications between two parties, allowing attackers to steal or manipulate information.
- Supply chain attacks compromise software or hardware before they reach consumers, exploiting trusted relationships to infiltrate systems.
In the following sections, we will delve into the complexities of these top cybersecurity threats and explore effective defense strategies for 2024.
Malware Threats
Malware, or malicious software, continues to pose a significant threat to cybersecurity across the globe. In 2024, we are witnessing a rise in the complexity and stealth of malware attacks, making them increasingly difficult to detect and mitigate.
- Primary types of malware that are particularly concerning this year:
Viruses and Worms
Viruses and worms, among the oldest forms of malware, remain effective due to their evolving techniques. Viruses attach themselves to clean files, spreading uncontrollably and damaging core system functionality while corrupting data.
Worms self-replicate without human intervention, often exploiting vulnerabilities in network systems. Recent variants have become adept at evading detection by mimicking benign network traffic.
Ransomware
Ransomware has seen a marked increase, with activity up 50% year-on-year in the first half of 2023, according to the World Economic Forum.
In 2024, the trend continues, as attackers encrypt victims’ files and demand ransom—typically in cryptocurrencies for anonymity—to restore access.
The rise of Ransomware as a Service (RaaS) has made it easier for even non-technical criminals to launch attacks, leading to greater frequency and sophistication.
Cryptojacking
Cryptojacking is a stealthy threat that hijacks computer resources for cryptocurrency mining. Unlike other malware forms that focus on theft or data compromise, cryptojacking quietly generates revenue without drawing immediate attention, making it particularly damaging in terms of resource utilization.
Fileless Malware
Fileless malware operates by leveraging scripts or modules loaded directly into the random access memory (RAM), avoiding detection by traditional antivirus solutions.
This type of attack exploits existing legitimate programs to execute malicious activities, often bypassing user and endpoint defenses.
To combat these malware threats, organisations should implement a layered security strategy that includes regular software updates, comprehensive end-user education to prevent phishing, advanced threat detection systems, and strict access controls.
Establishing a robust cybersecurity framework and conducting regular audits will aid in early detection and mitigation of these threats.
Social Engineering Attacks
Social engineering remains one of the most insidious types of cyber threats, exploiting human psychology rather than technological vulnerabilities.
These type of attacks manipulate individuals into bypassing normal security procedures, often resulting in significant data breaches or financial losses. Here’s how these schemes are evolving in 2024:
Phishing Variants
Spear Phishing: Spear phishing involves targeted attacks aimed at individuals, using highly tailored and convincing messages that often appear to come from colleagues or trusted sources.
For instance, attackers may pose as remote tech support agents addressing VPN issues, exploiting common workplace challenges to manipulate employees, particularly during periods of widespread remote work.
Vishing (Voice Phishing): In vishing scenarios, attackers use phone calls to extract sensitive information under the guise of legitimate requests. A typical scheme involves impersonators claiming to represent a bank, alerting victims to suspicious transactions, and coaxing them into verifying personal account details, which can ultimately lead to financial theft.
Smishing (SMS Phishing): This technique utilizes text messages that create a sense of urgency, prompting recipients to take immediate action, such as clicking a link to track an undelivered package. However, the link redirects them to a malicious site designed to compromise their personal data.
Baiting and Pretexting
Baiting: Baiting tactics lure victims with the promise of goods or information. A common method includes distributing USB drives that claim to contain important work-related data, like employee salary lists, but actually harbor harmful malware intended to infiltrate corporate networks.
Pretexting: Attackers frequently employ pretexting to acquire personal information under false pretenses. For example, they may pose as surveyors needing confidential data for supposed business or security audits, exploiting the trust and cooperative instincts of targeted individuals.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a sophisticated scam that employs email fraud to trick companies into transferring money or sensitive data to criminal actors.
In 2024, these schemes have become more intricate, with fraudsters conducting thorough research to convincingly mimic internal communications.
For instance, attackers may use compromised email accounts to request wire transfers, posing as urgent and confidential business dealings.
Often, these fraudulent emails are only identified as scams after the transaction has been completed, resulting in substantial financial losses for businesses.
To combat social engineering attacks like BEC, organisations must prioritize security awareness training for employees, helping them recognise and appropriately respond to such schemes.
Additionally, implementing multi-factor authentication (MFA) can significantly reduce the risk of successful breaches stemming from social engineering tactics.
Network and Application Attacks
As cyber threats evolve, network and application attacks have grown increasingly sophisticated, targeting the very foundation of organisational IT infrastructures. Here’s how these attacks are currently manifesting:
Distributed Denial of Service (DDoS) Attacks
DDoS attacks aim to overwhelm networks, servers, or websites with excessive traffic, depleting resources and bandwidth, thereby rendering services unavailable to legitimate users.
Amplification attacks have intensified this threat by leveraging publicly accessible servers, such as DNS (Domain Name System), NTP (Network Time Protocol), and SNMP (Simple Network Management Protocol), to significantly amplify the assault. This can cripple systems in a matter of minutes.
The scale and frequency of DDoS attacks have surged dramatically; from 2022 to 2023, the global average number of DDoS attacks per customer increased by 94%, with the Americas experiencing a staggering 196% rise.
This region accounted for nearly half of all DDoS attacks worldwide, highlighting the growing strategic use of DDoS in cyber conflicts and hacktivism.
Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks occur when attackers intercept and alter communications between two parties without their knowledge.
With the rise of encrypted traffic via HTTPS, these attacks have become increasingly sophisticated. Cybercriminals often exploit vulnerabilities in SSL/TLS protocols or utilize stolen certificates to decrypt and manipulate communications.
A common example of MitM attacks is WiFi eavesdropping, where attackers leverage unsecured WiFi networks to intercept user data.
Recent statistics reveal a 35% increase in MitM attacks reaching inboxes from early 2022 to early 2023, with a significant focus on targeting Office 365 authentication.
Additionally, these attacks frequently use URL redirects to disguise phishing sites, making them more difficult to recognise and block.
Injection Attacks
Let’s talk about injection attacks, those ever-looming nightmares haunting the world of web applications. Seriously, it’s like every day we hear about another breach because someone decided to throw caution to the wind and trust untrusted data.
What a brilliant idea! Attackers send malicious inputs to an interpreter, and voilà, the interpreter goes ahead and executes commands it should never have touched.
SQL Injection: Ah, SQL—the beloved backbone of data management. It’s also a playground for hackers! By slipping malicious SQL statements into input fields, attackers can manipulate databases to expose sensitive information, alter data, or even wipe it clean.
You’d think that after the countless breaches, developers would tighten up their queries, but no! It’s like they’re daring attackers to find the tiniest flaw. Recent breaches show that even the most minor mistakes can lead to massive data dumps. It’s infuriating!
Code Injection: Then we have code injection, where hackers inject malicious scripts into vulnerable applications. And what do those applications do?
They execute the code like it’s a friendly handshake! This is often seen in applications that evaluate user-stored code. What could possibly go wrong?
OS Command Injection: Don’t even get me started on OS command injection. Here, attackers gain the ability to execute shell commands on a server.
By manipulating input forms processed by application servers, they can run arbitrary commands and take full control of the operating system. It’s like handing over the keys to your digital kingdom to a complete stranger.
Defending Against Network and Application Attacks
Defending against network and application attacks necessitates a comprehensive, multi-faceted approach:
For DDoS Attacks: Implement robust threat monitoring systems to detect and mitigate attacks before they can inflict significant damage.
Utilising rate limiting—controlling the volume and speed of traffic to a network server—alongside web application firewalls (WAFs) and dedicated anti-DDoS hardware and software solutions is essential for effective defense.
For Man-in-the-Middle Attacks: Ensure proper SSL/TLS configurations, which are vital for secure communication over networks, and keep all certificates current.
Educating users about the importance of securing their internet connections, particularly on public networks, is also crucial in preventing these attacks.
For Injection Attacks: Employ rigorous input validation and utilize prepared statements with parameterised queries in databases to protect against unauthorized data access. Regularly reviewing and updating codebases is important to safeguard against emerging vulnerabilities.
Digital Infrastructure Threats
As technology evolves, it brings forth a new wave of cybersecurity challenges, particularly in the rapidly expanding realms of the Internet of Things (IoT), supply chains, and cloud computing.
These sectors are not only vital to organizational operations but have also become prime targets for cyberattacks, requiring urgent attention and robust defenses.
Internet of Things Attacks
The Internet of Things encompasses a vast network of devices—from everyday household appliances to critical industrial equipment—all interconnected online.
Unfortunately, many of these devices lack adequate security measures, rendering them vulnerable to exploitation. Common weaknesses include insecure firmware, weak authentication protocols, and unprotected network services.
For instance, compromised IoT devices can be transformed into botnets, unleashing large-scale DDoS attacks that can paralyze networks.
As the IoT landscape continues to expand, securing these devices becomes imperative, necessitating the creation of innovative security frameworks and the enforcement of stringent security practices during the development phase.
Supply Chain Attacks
Supply chain attacks exploit the intricate interdependencies of organizational systems, targeting trusted relationships to breach multiple entities through a single vulnerability.
High-profile incidents, such as the SolarWinds attack, have starkly illustrated the devastating impact of these threats, affecting thousands of businesses and government agencies alike by embedding malicious code within legitimate software updates.
Not to mention, such attacks can compromise the integrity of entire ecosystems, underscoring the urgent need for enhanced vigilance and fortified security protocols across supply chains.
Cloud Security
As businesses continue to embrace cloud computing, vulnerabilities within cloud infrastructure have come to the forefront. Misconfigurations and insufficient access controls are the primary culprits behind unauthorized access and data breaches.
A notable example is the improper configuration of S3 buckets, a core storage resource in Amazon Web Services (AWS), which has resulted in substantial data losses for even large corporations.
These incidents highlight the critical need for organisations to prioritize cloud security by implementing robust configuration management practices and stringent access control measures.
As reliance on cloud services grows, so does the imperative to safeguard sensitive data and maintain trust in these essential technologies.
Preventive Measures
To effectively counter these cybersecurity threats, organizations must adopt a series of preventive measures:
- IoT Security: Regular firmware updates, changing default credentials, and implementing network segmentation can substantially bolster the security of IoT devices, reducing the risk of exploitation.
- Supply Chain Security: Ongoing vetting of all partners, strict adherence to security standards, and the integration of security protocols into contract agreements are essential to protect the interconnected systems within supply chains.
- Cloud Security: Leveraging automated tools for monitoring and correcting configurations, enforcing rigorous access controls, and providing comprehensive training for employees on cloud security best practices are critical steps in safeguarding cloud environments against vulnerabilities.
State-Sponsored and Insider Threats
As the cyber landscape becomes increasingly politicized and competitive, state-sponsored cyber activities and insider threats have surged, presenting complex challenges to global security infrastructures.
Nation-State Cyber Activities
Nation-state cyber activities frequently focus on espionage, sabotage, and attempts to manipulate international political dynamics.
For instance, Russian government-sponsored groups have targeted critical infrastructure in the United States and Ukraine, employing malware and DDoS attacks to disrupt services and gather intelligence.
Similarly, Chinese cyber units have engaged in prolonged espionage campaigns against technology companies, aiming to steal intellectual property and sensitive government data.
The operations are marked by their sophistication, the substantial resources provided by state backing, and long-term objectives that align closely with national military or economic strategies.
Insider Threats
Insider threats stem from individuals within an organization who exploit their access to systems and data, whether out of malice or negligence. To detect and prevent these threats, organizations can adopt several strategies:
- Behavioral Analytics: Implementing user and entity behavior analytics (UEBA) can help identify anomalous behavior patterns that may signal malicious activity or violations of policy.
- Access Controls: Applying the principle of least privilege and regularly reviewing access permissions ensure employees only have access to the resources essential for their job functions.
- Regular Audits and Training: Conducting comprehensive security audits and providing ongoing security awareness training educates employees about the signs of insider threats and emphasizes the importance of adhering to organizational security policies.
Mitigation Strategies:
For nation-state threats, strengthening national cybersecurity policies, enhancing international cooperation, and developing counter-cyber espionage strategies are vital. Organisations should invest in cybersecurity intelligence to anticipate emerging threats posed by foreign governments.
For insider threats, it is crucial to establish a clear policy outlining acceptable behaviors, integrate robust data loss prevention (DLP) technologies, and maintain an up-to-date incident response plan that includes specific provisions for insider incidents.
Privacy Concerns and Data Breaches
,Privacy concerns and data breaches are pressing issues for organizations globally. Regulatory changes and compliance with international laws play a crucial role in shaping cybersecurity strategies, while insights gained from major breaches inform necessary security enhancements.
Regulatory Changes and Compliance
International regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), have significantly transformed cybersecurity approaches.
The laws impose rigorous data protection requirements, compelling organizations to implement strong measures to safeguard consumer information, with severe penalties for non-compliance.
For example, GDPR mandates prompt data breach notifications, which have necessitated that companies bolster their incident response strategies to quickly detect and address breaches.
Ensuring compliance not only fulfills legal obligations but also fosters consumer trust by demonstrating a commitment to protecting personal information.
Organisations that prioritize privacy and data security are better positioned to navigate the complex regulatory landscape and maintain the confidence of their stakeholders.
Recent Data Breaches (2024)
- AT&T
Records Breached: 7.6 million current and 65.4 million former customers infiltrated AT&T’s systems, compromising personal data of both current and former customers, including sensitive information like Social Security numbers, account numbers, and passcodes.
The exposed data, originating from 2019 or earlier, surfaced on the dark web in mid-March 2024. This breach follows a January 2023 incident that affected nine million users.
AT&T is conducting an investigation to mitigate malware spread while ensuring systems remain operational for current customers, amidst threats of multiple class action lawsuits.
- MOVEit
Records Breached: 77 million. MOVEit, a Managed File Transfer (MFT) application utilised by numerous organisations and government agencies, suffered one of the largest breaches in 2023.
The CLOP malware gang exploited a security vulnerability to deploy ransomware, leaking confidential data of 77 million individuals and over 2,600 companies globally.
U.S. entities were notably impacted, with 78% of breached companies being American, including the U.S. Department of Energy and several universities. The total global damages are estimated to exceed $12 billion.
- Ticketmaster Entertainment, LLC
Records Breached: 560 million. In May 2024, hackers accessed and leaked over 560 million customer records from Ticketmaster, including order history, payment information, and personal details.
The company has alerted its customers to monitor their accounts and credit statements. In response, the Justice Department is preparing to file a federal antitrust lawsuit against Live Nation, Ticketmaster’s parent company.
- Tile
Records Breached: 450,000. In June 2024, Life360, the maker of the Tile tracker device, announced a data breach affecting 450,000 users.
The stolen data includes names, addresses, email addresses, phone numbers, and purchase order details. Additionally, hackers accessed tools that can process location requests from law enforcement and are now extorting Life360 for ransom.
- Dell
Records Breached: 49 million. In May 2024, Dell experienced a substantial cyberattack affecting approximately 49 million customers. The hacker, known as Menelik, disclosed to TechCrunch that he extracted large volumes of data by creating partner accounts within Dell’s company portal.
After gaining access, he launched brute-force attacks, submitting over 5,000 requests per minute for nearly three weeks, during which Dell was unaware of the breach.
While no financial details were reportedly compromised, sensitive customer information like home addresses and order data may have been exposed, and the data is believed to be for sale on hacker forums.
- Bank of America
Records Breached: 57,000. In February 2024, Bank of America reported a ransomware attack affecting over 55,000 customers via Mccamish Systems, one of its service providers.
The breach involved unauthorised access to personal information, including names, addresses, Social Security numbers, and account details.
The breach was detected through routine security monitoring on November 24, yet customers were only notified on February 1, roughly 90 days later, suggesting a potential violation of federal notification laws.
Major Data Breaches
Recent high-profile data breaches have starkly exposed vulnerabilities in cybersecurity defenses, reinforcing the urgent need for enhanced security measures. Notable examples include:
Equifax Breach
One of the most significant breaches in history, the Equifax incident compromised the personal information of approximately 147 million consumers.
The breach was attributed to an unpatched vulnerability in a web application, underscoring the critical importance of effective patch management and timely updates.
Capital One Breach
The Capital One breach involved the theft of data from over 100 million customers, stemming from a hacked web application firewall.
The incident highlighted the necessity for thorough security configurations and the importance of routine security assessments to safeguard sensitive information.
Addressing Cybersecurity Risks
To effectively mitigate cybersecurity risks, organizations should implement the following preventive measures:
- Continuous Monitoring and Updates: Regularly update and monitor systems to guard against emerging vulnerabilities.
- Enhanced Incident Response: Develop and rehearse incident response protocols to manage data breaches efficiently, ensuring swift mitigation and compliance with breach notification laws.
- Education and Awareness: Provide ongoing training for employees on cybersecurity best practices and phishing recognition to minimize the risk of human error.
- Compliance Audits: Conduct regular audits to ensure all systems adhere to relevant international and local privacy laws.
- Advanced Security Infrastructure: Invest in cutting-edge security technologies, including encryption, intrusion detection systems, and comprehensive endpoint security to reduce data breach risks.
- Third-Party Risk Management: Implement rigorous security assessments and controls in all third-party contracts to prevent breaches through vendors.
Advanced Persistent Threats (APTs)
APTs are complex cyberattacks designed primarily to steal information or sabotage operations, often targeting national governments, infrastructure, and large corporations.
These threats unfold over extended periods, making them discreet and particularly dangerous due to the strategic planning involved.
Characteristics of APTs
APTs are marked by their sophistication and persistence, with attackers focusing on long-term objectives while avoiding detection. Key characteristics include:
- Highly Targeted: Attackers invest significant time and resources to tailor tactics based on the vulnerabilities and value of specific entities or sectors.
- Long-Term Engagement: APTs often involve prolonged engagement with a target’s network, sometimes spanning years to continuously extract data or wait for opportune moments to strike.
- Use of Advanced Malware: These attacks frequently employ sophisticated malware and spear-phishing methods to gain initial access and maintain persistence within the target’s infrastructure.
- Evasion Techniques: APTs utilize advanced methods to evade detection, including encryption, kill switches, and the exploitation of zero-day vulnerabilities.
- Lateral Movement: After gaining access, attackers move laterally through the network to establish footholds across various segments of the organization’s digital infrastructure.
Defending Against APTs
To counter APTs, organisations must adopt a multi-layered approach that integrates advanced security technologies with vigilant monitoring and rapid response strategies. Effective prevention and defense measures include:
- Regular Security Assessments: Continuously evaluate and update the organization’s security posture to adapt to emerging threats.
- Encryption: Encrypt sensitive data at rest and in transit to minimize the value of intercepted information.
- Threat Intelligence Sharing: Engage in industry and government cybersecurity initiatives to receive early warnings about new APT tactics and remediation techniques.
- Segmentation and Zero Trust: Implement network segmentation and a zero-trust security model to limit lateral movement and restrict access to critical information.
- Advanced Detection Technologies: Utilize behavior-based threat detection systems that can identify anomalies indicative of APT activities, such as unusual network traffic or unexpected data flows.
- Incident Response and Forensics: Develop a comprehensive incident response plan that includes forensic capabilities to investigate and address breaches following an APT attack.
- Continuous Monitoring and Updating: Regularly update security systems and software to protect against known vulnerabilities while performing continuous monitoring of all network activity for prompt threat detection and response.
- Employee Training and Awareness: Educate employees about the risks and indicators of APTs, particularly focusing on spear-phishing and social engineering tactics, as human factors often represent the weakest links in security.
The Ongoing Shortage of Cybersecurity Professionals
The cybersecurity workforce shortage has reached an alarming crisis point, with nearly 4 million unfilled positions worldwide, despite a 10% increase in the workforce over the past year.
This troubling trend highlights the growing demand for qualified cybersecurity professionals, as the workforce gap has expanded by 12.6% year-over-year, according to the latest Cybersecurity Workforce Study by ISC2.
Two-thirds of cybersecurity professionals indicate that their organizations do not have sufficient staff to effectively prevent and address security issues.
The deficit is exacerbated by economic uncertainties, budget cuts, and hiring freezes, which fundamentally undermine organizations’ ability to maintain robust cybersecurity defenses.
Moreover, the skills gap is proving to be even more critical than the sheer number of unfilled positions. Areas such as cloud computing security, artificial intelligence, machine learning, and zero-trust implementation are particularly underserved.
A staggering 92% of companies report a skills gap in essential cybersecurity areas, and according to Forbes, “these gaps can lead to everything from irresponsible handling of personal information to catastrophic infrastructure failures with potentially life-threatening consequences.”
This persistent shortage, coupled with the widening skills gap, presents a significant opportunity for individuals considering a career in cybersecurity.
Pursuing advanced education and training can equip aspiring professionals with the critical knowledge and skills necessary to fill these gaps and meet the escalating demands of the field.
What Companies Are Doing to Combat Cybersecurity Threats
To effectively prevent and mitigate cybersecurity threats, companies are increasingly prioritizing cybersecurity education.
Many organisations are leveraging webinars and training tools to keep employees informed about best practices and protocols, ensuring everyone understands their role in maintaining security.
In addition to education, companies are adopting advanced technologies and conducting regular security audits. Many are also hiring experienced cybersecurity professionals or consultants to bolster their defenses and navigate the evolving threat landscape.
Recognising the need for specialized training, the University of San Diego has developed two master’s degree programs tailored to address the pressing challenges in cybersecurity today.
The innovative online Master of Science in Cyber Security Operations and Leadership, alongside the Master of Science in Cyber Security Engineering—offered both on-campus and online—aims to equip the next generation of cybersecurity professionals.
Strategies companies are implementing to combat cybersecurity threats:
- Cybersecurity Education: Conducting webinars and training sessions to inform employees about best practices and protocols.
- Advanced Technologies: Adopting new security technologies to enhance defenses against cyber threats.
- Regular Security Audits: Performing security assessments to identify vulnerabilities and strengthen overall security posture.
- Hiring Experts: Bringing in experienced cybersecurity professionals or consultants to bolster internal capabilities.
- Incident Response Planning: Developing and rehearsing incident response protocols for effective breach management.
- Investment in Security Tools: Implementing advanced security solutions such as firewalls, intrusion detection systems, and endpoint security.
- Data Protection Measures: Utilising encryption and data loss prevention (DLP) technologies to safeguard sensitive information.
- Collaboration with Industry Groups: Participating in cybersecurity initiatives and information-sharing networks for threat intelligence.
- Compliance with Regulations: Ensuring adherence to relevant cybersecurity regulations and standards to mitigate legal risks.
- Building a Security Culture: Fostering a workplace culture that prioritises security awareness and encourages employees to report suspicious activities.
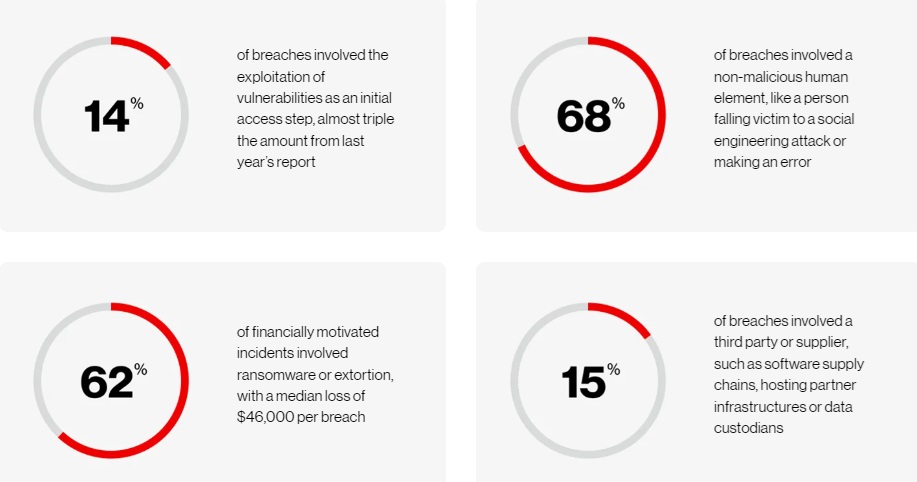
A Study Of 30,458 Cyber Threat Incidents
Verizon’s 2024 Data Breach Investigation Report analysed 30,458 cyber threat incidents, revealing 10,626 confirmed data breaches.
The findings indicated that approximately one-third of these breaches involved ransomware or other extortion methods, accounting for 32% of the incidents examined. Notably, ransomware emerged as the primary threat, impacting 92% of industries surveyed.
Over the past three years, ransomware and various extortion tactics—such as phishing, malware, and DDoS attacks—have contributed to nearly two-thirds of all data breaches, with their prevalence fluctuating between 59% and 66%. (DBIR 2024)
Top Takeaways
Explore a preview of some of the cybersecurity data uncovered by this year’s DBIR.
Reflecting On The 2023 Cyber Threat Landscape
As we examine the cyber threat landscape of 2023, a clear theme emerges: stealth. Adversaries have been met with a fortified attack surface, thanks to significant advancements in threat defense technologies and heightened awareness among organisations.
In response, cybercriminals have adapted by increasingly adopting techniques that enable rapid movement and evasion of detection.
The prevalence of eCrime stands out as a particularly striking trend this year, serving as a highly attractive and lucrative avenue for many criminals.
Unsurprisingly, eCrime has remained the dominant threat, with adversaries deploying strategies designed to maximize stealth, speed, and impact.
Ransomware continues to be the weapon of choice for many high-profile attackers targeting valuable data. However, the landscape is shifting as data-theft extortion has emerged as an appealing—often simpler—method of monetization.
The shift is underscored by a staggering 76% increase in the number of victims listed on dedicated leak sites (DLSs) associated with big game hunting (BGH) adversaries between 2022 and 2023.
Access brokers have thrived by supplying initial access to eCrime actors throughout the year, with advertised access increasing by 20% compared to the previous year. This trend highlights the growing interconnectedness of cybercriminal networks.
Nation-state adversaries have also remained active, with those aligned with China operating at an unprecedented pace on the global stage. Leveraging stealth and scale, they have focused on gathering surveillance data, strategic intelligence, and intellectual property from targeted groups.
Elsewhere, geopolitical conflicts have fueled cyber activity. As the Russia-Ukraine war continued into its second year, Russia-nexus adversaries maintained a high level of sustained activity, supporting intelligence collection efforts by the Russian Intelligence Service.
In 2023, eCrime remained a cornerstone of the cyber threat landscape, with notable activity attributed to adversaries like SCATTERED SPIDER and GRACEFUL SPIDER. These groups have significantly influenced the dynamics of cybercrime, particularly in the realm of big game hunting (BGH).
CrowdStrike’s Chief Analytics Officer (CAO) has assessed that BGH will continue to be the dominant threat in the eCrime landscape throughout 2024.
The conclusion is drawn with high confidence, reflecting the ongoing success of these operations, as evidenced by the remarkable 76% increase in posts on dedicated leak sites (DLSs) this year.
Looking ahead to 2024, we can expect to see several trends emerging in support of BGH operations. Notably, ransomware-free data leak initiatives may become more prevalent, allowing adversaries to capitalize on stolen data without resorting to traditional ransomware tactics.
Additionally, an increase in cloud-focused operations is anticipated, reflecting the evolving nature of cybercrime as attackers adapt to new technological environments and targets.
Top Cyber Security Threats 2024 – Conclusion
As we navigate through 2024, the cybersecurity landscape presents a myriad of evolving threats that require heightened awareness and proactive measures from organizations worldwide.
Key trends indicate that cybercriminals are becoming increasingly sophisticated, employing advanced techniques that exploit vulnerabilities across various sectors.
Ransomware continues to dominate, evolving from traditional attacks to more nuanced approaches, such as ransomware-free data leak operations.
The shift reflects a broader trend among adversaries to seek more effective monetization routes, with data-theft extortion gaining traction.
2024 demands that organizations adopt a multi-layered cybersecurity approach, integrating advanced technologies, continuous monitoring, and employee education.
By staying informed about the latest threats and evolving tactics used by adversaries, businesses can better position themselves to defend against potential attacks







