According to estimates data and other cyber security breaches is projected to cost global businesses $10.5 trillion annually. Businesses need to invest in robust cybersecurity defenses to prevent data breaches from occurring includeding implementing multi-factor authentication, conducting regular security audits, and providing regular training to employees
The technological disruptions that are occurring today in multiple industries continue to create opportunities for tech service companies. This is good news for companies that provide solutions in software, cloud storage or artificial intelligence.
You’ll want to start by assessing the needs of a tech-startup. Here are some steps you can take to build a solid foundation for your business.
1. Idea and Brand
You need an idea of a service or product that you would like to offer. It can be a product or service that you have seen as a solution to a problem.
You can create a brand around your idea once you’ve got it. The brand can define the unique “personality of your company”
2. Market and Customers
You should also validate your idea with customers or users in order to make sure that it is something people want. How can you do this? Start by conducting market research for your product.
Check if your product has a market, or if it is similar to another. There is definitely a demand for what you offer if both are present. Then you can identify a audience around which to base your product and strategy.
3. The Team
It’s time for you to start building your team once you have your market and your idea. It’s important to assemble a team of co-founders, subject matter experts and other people who share your vision. You can then hire employees or developers with the necessary skills to bring your vision to life.
The majority of tech startups hire offshore developers. It is an affordable way to develop new software as you build a tech company.
4. Funds
Funding is the next element to consider when creating a new startup. Your tech startup will need capital. You can contact investors or institutions if you do not have any personal savings. They include, among others:
- Angel investors
- Accelerators/incubators
- Venture capitalists
You can contact these institutions to get assistance in starting a tech company as a nontechnical person. They can offer more than just money. Investors have a wealth of experience in the tech industry that you can use as a budding businessperson.
Cybersecurity Risk Management Business Tips
Cybersecurity breaches have been on the rise, and it’s expected that by 2023. While technology has made it easier for organisations to upgrade security measures, malicious hacker are now using sophisticated software.
In order to minimise your cybersecurity risks, it is important to implement strict cybersecurity policies and take proactive measures.
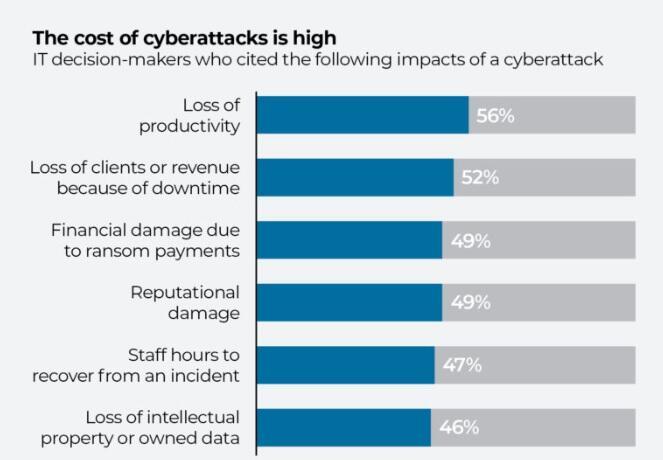
You can’t leave the data protection to chance. It could have a huge impact on your business, resulting in revenue loss, disruption of operations, and theft of customer data.
In some cases, data breaches can also lead to reputational damage, which could put you out of business. How can you lower cybersecurity risks for your business, given all that is at stake? Here are 10 strategies you can implement.
1. Secure data and create backups
Make sure that all sensitive data is encoded. Your data will be easier to hack if you save it in plain text. Data encryption on the otherhand limits access to data only for parties who have the encryption key.
The encryption ensures that unauthorized parties cannot read the data even if they gain access. Data encryption software can even alert you when someone tries to change or alter the data.
Backups of important data should be performed regularly. Data loss can sometimes be caused by cybersecurity breaches. If you do not have a secure and reliable backup, this could lead to operational disruptions and loss of revenue for your business. 3-2-1 Rule is one of the best data backup strategies.
According to this strategy, your data should be stored in at least three copies. Two of the copies should be on different media and one in an offsite location.
2. Employees should be trained regularly
Phishing emails sent to employees are one of the most common ways hackers can gain access to a database. Statistics show that more than 3.4 billion phishing email have been sent worldwide. These emails are containing malicious malware that is sent in the form links. This gives hackers access to data including login credentials.
It is difficult to detect phishing emails because they look legitimate. Hackers may, for example, send emails impersonating company leaders and ask for details. The employee could end up disclosing the information without proper training. It is therefore vital to conduct cybersecurity training. Inform your employees about the most common forms of cyber attacks and how to best prevent them.
It is also important to stress the importance of double-checking email addresses and links before responding or clicking. Don’t forget the organisation policy on sharing sensitive information even via social media.
3. Update software and systems
Updates to your software and systems have a significant impact on cyber security. They not only fix bugs but also help patch security flaws vulnerabilities.
Hackers who are malicious write code to exploit vulnerabilities. This code is often packaged as malware that can impact your entire system. Use a patch management program to manage updates automatically and maintain information security.
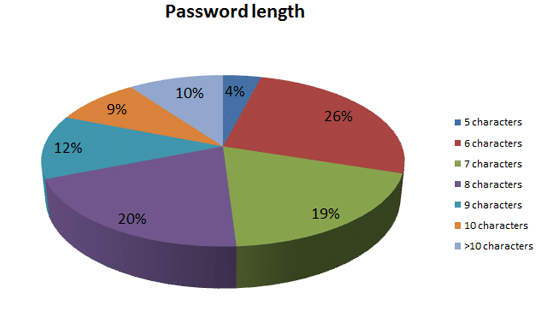
4. Strong Passwords
A fascinating fact: 80% of data breaches in organisations are caused by weak passwords. Hackers do not need to be very skilled to access your system. Hackers only need a small hole to exploit.
Simple passwords are no longer sufficient. Password cracking technologies have advanced greatly. To discourage cybercrime, it is better to deploy multi-factor authentication and use complex passwords. It is important to discourage employees from sharing passwords so that, even if one computer is compromised the rest are still secure.
- Passwords are a great way to mitigate security risks.
- At least eight characters should be included in all passwords.
- The characters should be alphanumeric.
- You shouldn’t include any personal information.
- The product should be original and un-used before.
- The words should be spelled correctly.
- Keep your password in an encrypted form.
With many employees now working from home, bring-your-own-device (BYOD) is becoming increasingly common. Recommend iOS users to activate the Security recommendations feature in order to monitor the strength and security of their passwords.
5. Asses your vendors
You cannot ignore vendor risk management because your cyber security depends heavily on third-party vendors. You can use this to mitigate third-party risks instead of relying solely on incident response.
You should focus on:
- Cybersecurity Risk: Onboard vendors with the right strategies, and monitor their performance throughout your relationship.
- Legal, regulatory and compliance risks: ensure that the vendor won’t impact your compliance with local laws, regulations and agreements.
- Operational Risk: If the vendor is an important part of your business, make sure they will not disrupt your operations.
- Risk assessment: Ensure that the vendor does not affect your ability to achieve your organization’s objectives.
6. Get Cyber Liability Insurance
Cyber security incidents are becoming more severe. A cyber insurance policy can help you manage the risks posed by cyber-attacks. This should be considered in conjunction with other risk management techniques, such as the development and regular review of cyber risk management, controls, and risk assessments.
Many startup businesses and business owners believe that their company is too small for cybercriminals to target. Cyber theft is not a matter of size. Tech startup insurance can protect your startup IT against cyber threats and data breaches.
Understanding cyber risk, controls and compliance may seem overwhelming. To protect your business from the effects of a cyber-attack, you need to understand each concept.
7. Install Firewalls
Cyber attacks are getting more sophisticated and hackers find new ways to access data every day. Installing firewalls will protect your network from cyber-attacks. A reliable system can protect you against brute force attacks and prevent security incidents that could cause irreversible damages.
Firewalls also monitor network traffic in order to detect any suspicious activities that may compromise the integrity of your data. Additionally, they prevent sophisticated spyware from accessing your systems and promote privacy.
When choosing the firewall that is right for your business, be very cautious. Choose a system which gives you complete security control, visibility and monitoring of your applications and networks. It should have prevention and protection capabilities, as well as an streamlined security architecture.
8. Take Security Seriously
The majority of cyber-risk management policies are based on digital aspects and ignore the physical location. Assess your critical infrastructure to determine if it is protected from security breaches. Analyse your data protection policies and determine if they have data disposal strategies.
Imagine a situation where your online systems were safe from cybercriminals but you experienced a breach when someone broke into your office and went through your filing cabinets.
This would be tragic. Even other cases have been reported where janitors have retrieved personal information from customers and employees by going through garbage.
You should also use 2-factor authentication such as keycards and biometrics. Use 2-factor authentication, such as biometrics and keycards. Even if your keycard is stolen or lost, you will still be unable to gain access.
9. Install a Killswitch
A killswitch will protect you from large-scale cyber attacks. This is a reactive strategy for cybersecurity protection where your IT department will shut down all systems when they detect something suspicious.
Cybercriminals are not very good at hiding their tracks. This is especially true when they do not expect to be caught. Your IT security team should regularly analyse server logs and perform cybersecurity framework audits in order to ensure their integrity. You should also invest in tools for network forensics analysis that can analyse the information flow on your network.
Human error is the main cause of malicious attacks and ransomware. Some are caused by employees. Statistics show that 94% of organisations have suffered cyber threats as a result of insider breaches.
You should scan new employees to ensure they don’t pose a cyber threat to your company. It is important to take measures to reduce employee negligence which can be a significant contributor to cyber-risks.
10. Develop a Secure Cybersecurity Policy
The policies you implement will have a significant impact on the cybersecurity of your organisation. Do you have Guidelines for Data Breach Prevention and Detection in place? How often does your IT team conduct penetration testing or risk assessments? Your guidelines are the first step!
Identify any gaps in your policies. You should also have the following guidelines in place:
- Disaster Recovery: In the event of a security breach, your IT team and employee will know what to do next. The plan is designed to minimise the time you’re offline and ensure that your business can resume operations as quickly as possible.
- Control/management : This policy highlights who can access sensitive data, reducing the risks of unauthorised access. Mishandling data can have both legal and financial consequences. Make sure that your access management policy specifies who has access to which information and when.
- Security Testing : The policy should specify the frequency of cybersecurity tests. You can then uncover any vulnerabilities before they become critical. You should perform security tests such as vulnerability scanning, security assessment, penetration testing and ethical hacking.
- Incident Response Plan : This is documentation that outlines the steps and procedures to be followed in the event of a security breach. This also emphasizes the importance of information security and helps reduce your organisation’s response times.
Be sure to include a clause in your plan that outlines the consequences for data mishandling and the legal actions that will be taken against employees who are responsible. This will deter insider attacks.
Australian Cyber Crime Statistics
- Cyber crime costs Australian businesses $1 billion annually – yet it remains one of the least insured policy areas.
- ‘Unisys Security Index – Australia, 2019’ revealed that 15% of Australians would stop dealing with an organisation if their data was breached.
- In 2021 63% of organisations suffered a Cyber security breach!
- There were 497 notifiable data breaches reported between July and December 2022, a 26 percent increase on the first half of the year. Reports say five breaches affected more than 1 million individuals
About BizCover™ – Small Business Insurance
BizCover™ set out to give small businesses a fair go – in an industry dominated by big players, time consuming paperwork, lack of transparency and poor service levels.
They boldly disrupted the insurance market by creating BizCover, an online service to simplify comparing and buying business insurance from some of Australia’s leading insurers.







