There is no issue of greater concern to telecommunications service providers (telcos) than data security. Relied on for critical services, telcos devote significant resources to protecting their customers and operations from unauthorised data access and disclosure.
Up to now, that’s made many reluctant to shift their network operations and management to software-as-a-service (SaaS) models that rely on the public cloud.
However, as cost savings, speed and business agility increasingly become competitive must-haves, telcos need to overcome this historical reluctance and seize the full benefits of SaaS.
Three key segments make up the cloud computing market — Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS). Together, these segments allow users to access software, store data and develop new apps 100% remotely.
This white paper looks at how key questions around telecom SaaS security have been answered by leading public cloud providers including AWS, Google Cloud and Microsoft Azure, and SaaS providers
Introduction
Trust is at the core of the relationships between telcos and their customers. It is earned
by reliably handling and protecting massive volumes of data at rest, in transit and in use,
and ensuring the uninterrupted availability of business-critical and societally essential
services while meeting stringent security requirements.
What is telecom SaaS?
Telecom SaaS is subscription-based, cloud-native software service that delivers solutions to achieve specific business outcomes. It enables a fully digitalised business experience and fully automated services lifecycle for any carrier-grade network.
Given what’s at stake, telcos have held back from adopting software-as-a-service (SaaS) for network operations and management. They’re used to owning all aspects of the network and securing its perimeter how they see fit. Switching from on-premises infrastructure to the cloud might understandably seem risky.
Yet telcos are especially well positioned to gain by adopting SaaS because they can be both SaaS consumers and SaaS providers. By leveraging the services offered by SaaS and cloud providers, telcos can deliver subscription-based services to their own customers as interest grows in telco-specific SaaS offerings like network-as-a-service (NaaS) and network-slice-as-a-service (NSaaS).

What influences telecom SaaS security?
As enterprises continue to adopt SaaS, they are proving the benefits of cloud-based software delivery: faster rollouts of new services and accelerated time to value, lower upfront capital expenses, automated software upgrades and generally greater agility to respond to market conditions as they evolve.
Telcos have been reaping similar benefits by adopting SaaS for business support system (BSS) functions such as order-to-cash processing but have so far been reluctant to go all-in on SaaS for analytics, security assurance or network management due to concerns about data security, privacy, residency and sovereignty.
Security is key to getting full value from their investments in 5G, which requires evolving from closed pipe networks to open ecosystems. That demands zero-trust architectures, extended threat detection and response (XDR) capabilities, digital certificates and other strategies to mitigate risk.
The public cloud raises questions of how to ensure end-to-end security of SaaS data and workloads when the infrastructure is shared and provided by an external party.
The answers involve three interdependent layers in telecom SaaS and the public cloud, each one the domain of a different party:
- The infrastructure layer — offered by public cloud providers
- The SaaS user’s network layer — the traditional telco arena
- The application layer — where SaaS providers deliver their services
Figure 1. Defence-in-Depth – CNS SaaS six security layers
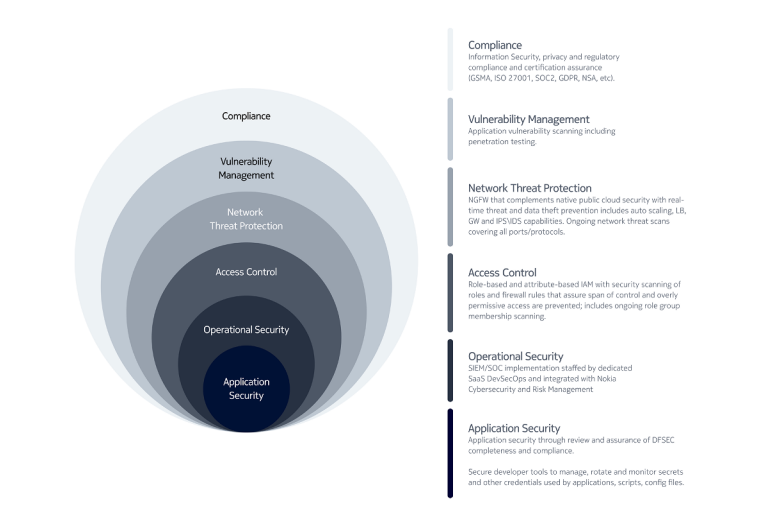
One of the first and most important steps in any public cloud SaaS deployment is clarifying the
relationships, responsibilities and boundaries among the parties responsible for these layers.
This is commonly referred to as the Shared Responsibility Model, defined by the UK National Cyber Security Centre as the fundamentals of who looks after the security of your data and services.
As with any outsourcing agreement, there is a joint responsibility for the security and availability of data and workloads in a cloud service that is shared between the cloud provider and the customer of that service.
The amount of responsibility that each party must own will depend on the type of service and how the service provider has chosen to implement it.
Under the Shared Responsibility Model, cloud service providers are responsible for securing the
infrastructure (hardware, software, networking and facilities) that their cloud services run on.
Public cloud providers must adhere to international standards when designing and operating their security program and controls (i.e., protections and countermeasures put in place to minimize and facilitate response to security risks).
Independent third-party auditors constantly verify this, issuing certifications and audit assessments that cloud service providers make available to their customers as proof they are fulfilling their portion of the Shared Responsibility Model.
SaaS providers are responsible for security within the cloud. That includes correctly configuring and managing any infrastructure services they use and designing and operating their applications securely.
SaaS consumers (in this case, telcos) remain responsible for securing network content and complying with regulations.
Their responsibilities include implementing proper identity and access management (e.g., strong passwords, multi-factor authentication, access and policy controls) and securely connecting to and using the SaaS (e.g., use of Transport Layer Security endpoints and properly configured encryption).
With this three-party model, telcos benefit from the cloud and SaaS providers’ best practices and investments in security, resulting in a highly secure SaaS environment.

Telcos can trust SaaS security
Industry experts believe that SaaS is as secure as on-premises software,
Just as telcos recognise the importance of the critical services they support, cloud service providers are relied on by customers in virtually every industry imaginable, including the highest levels of government, the financial sector and the military.
At any point in time, at least one-quarter of the world’s Internet traffic runs through the public cloud. Because cloud service providers operate at scale, their security practices need to be uniform and designed for the highest levels of protection.
It also enables telcos to benefit from the same high standards used by organisations with the most stringent security requirements, such as banks.
At the same time, serving many customers across all sectors around the world has given cloud providers unparalleled exposure and insight into security incidents and vulnerabilities, enhancing and accelerating their ability to identify, mitigate and prevent a broad range of cyber threats

As public cloud providers’ brand reputations depend on maintaining security and privacy, they have made massive investments in technologies, people and resources to build top-tier capabilities in security at scale.
Plus, the scale and economics of the cloud make it possible for cloud providers to invest more in security than any single enterprise alone. That includes spending on systems, technologies and techniques to address the four primary areas of SaaS concern, which apply to enterprises across all sectors (and not just telcos):

SaaS and data security
THE ISSUE: Protecting data from unauthorised access and rapidly identifying and containing security incidents when they occur. Public cloud providers understand their businesses hinge on meeting customer expectations of data security.
They also provide extensive frameworks and systems, and work with customers and partners to ensure clear, mutual understanding of the responsibilities at each layer.
Security is a core pillar of AWS’ Well-Architected Framework, built into Google Cloud’s trusted infrastructure approach and acknowledged by Microsoft Azure as “job one in the cloud”.
Some specific elements used across leading public cloud and SaaS providers include:
- Defense in depth: Protecting data and other assets with multiple layers of security, network
segmentation and boundary protection, traffic logging and monitoring, host-based intrusion detection and prevention, vulnerability assessments and remediation. - Isolation: Ensuring system reliability engineers (SREs) and all other personnel can’t access customer data, or the hardware that data runs on, without authorisation. This would mean, for example, that an infrastructure SRE is restricted from accessing application workloads permitted for application SREs.
- Durability and availability: Ensuring the integrity of customer data and its availability using technical measures such as backups and replication that ensure data is durable.
To build trusted relationships, cloud providers are transparent with customers about the controls
they have in place to secure the cloud.
“Transparency reporting has emerged as a valuable practice to demonstrate transparency and accountability,” according to IDC2.
This includes transparency with respect to the cloud provider’s technical, contractual and institutional obligations, as well as providing timely and proper notification and reporting of any security incidents and the related regulatory mandates involved, such as the EU’s General Data Protection Regulation (GDPR).
All major cloud and SaaS providers will provide audit reports when requested by customers, highlighting in detail which certifications they have received from organisations such as the International Organisation for Standardisation (ISO 27001), the Cloud Security Alliance (CSA), the GSM Association (GSMA), or System and Organisation Controls 2 (SOC2) auditors and others.
(By earning these certifications, cloud and SaaS providers relieve telcos from the burden of having to do the same, which can be a costly and timeconsuming process.)
The cloud and Saas providers will also provide detail on how they work to maintain compliance with security requirements.
To ensure data availability in the event a node dies or a data center goes offline due to a cyberattack or natural disaster, the cloud provider will replicate and sync the affected data to another data center in the same city or region. This provides the highest levels of resilience and availability while adhering to relevant data residency laws.

Demystifying SaaS and public cloud security – 2024
Demystifying SaaS and public cloud security is paramount in today’s digital landscape where organisations increasingly rely on these technologies to drive efficiency and innovation.
By understanding the shared responsibility model, implementing robust security measures, and fostering a culture of continuous monitoring and improvement, businesses can mitigate risks and reap the full benefits of SaaS and public cloud services.
Embracing security as a collaborative effort between cloud providers and users is essential in safeguarding sensitive data, maintaining compliance, and building trust with customers.
As the technology landscape continues to evolve, staying informed, proactive, and adaptable will be key in ensuring the security and resilience of cloud-based environments.







