Sextortion scams are a type of extortion where criminals attempt to extort money from victims by threatening to release explicit images or videos unless demands are met.
Leveraging usernames and passwords stolen in data breaches, criminals contact victims and claim to have compromising content, allegedly from the victim’s computer, and threaten to publicly share it if victims don’t pay up.
- Barracuda threat researchers have identified evolving tactics being used by cybercriminals in targeted sextortion scams.
- Criminals are now frequently using victims’ addresses and photos of their homes to better personalise sextortion phishing attacks and increase the pressure to pay.
- Extortion demands are increasing from hundreds to thousands of dollars, and criminals are making it easier for victims to pay with quick response (QR) codes.
Evolving Tactics Add Personalisation And Pressure
Barracuda research shows that extortion emails make up roughly 3% of the total number of targeted phishing attacks detected annually.
Most of these are sextortion attacks. Every incident is a serious crime with potentially devastating impact that can range from monetary loss to significant emotional and mental distress.
Barracuda researchers have identified evolving tactics — including advanced personalization — being used by criminals in these targeted attacks.
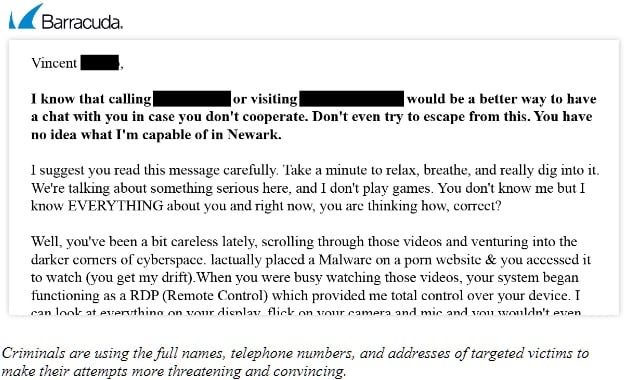
Criminals are leveraging the personal data of targeted victims, including full names, telephone numbers, and addresses, to make their sextortion attempts more threatening and convincing.
The sextortion emails address the victim by their first and last name, and the opening sentences of the email include the victim’s telephone number, street address, and city.
In many cases, emails start with copy like this: “I know that calling [telephone number] or visiting [street address] would be a better way to have a chat with you in case you don’t cooperate. Don’t even try to escape from this. You have no idea what I’m capable of in [city].”
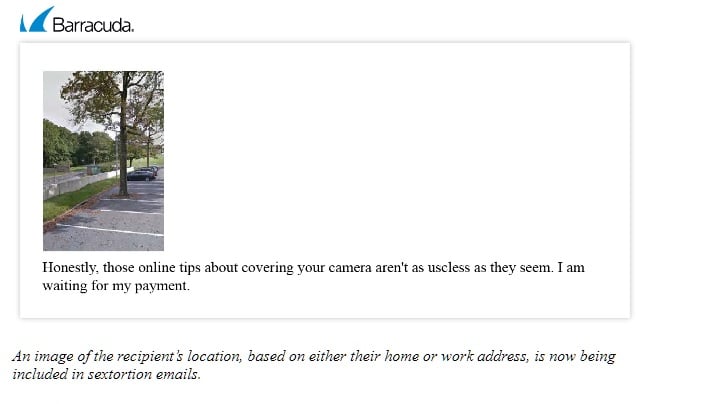
An image from Google Maps of the target’s location is now frequently being included in the sextortion email. In analyzed emails, images included either a residential or commercial location, depending on the address associated with the victim’s stolen data.
The Payment Demands Are Increasing.
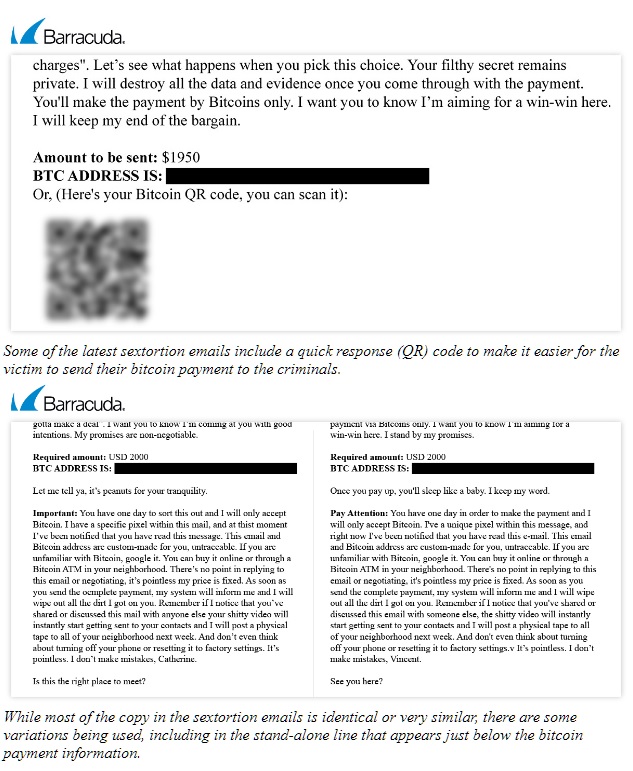
In the past, sextortion emails typically demanded payments of a couple hundred dollars, up to about $500 maximum. In the latest attacks seen by Barracuda researchers, the amounts are $1,950 and $2,000.
Different copy variations are being tested. While most of the copy in the emails is identical or very similar, there are some variations.
For example, several variations are being used in the line of copy that appears just before the Google Map image of the victim’s address, including:
- See you here?
- Can you notice something here?
- Is this the right place to meet?
Likewise, variations are being used in the line of copy that appears just below the bitcoin payment information, including:
- Once you pay up, you’ll sleep like a baby. I keep my word.
- Let me tell ya, it’s peanuts for your peace.
- Let me tell ya, it’s peanuts for your tranquility.
Additional Points Of Personalisation Are Being Used.
In some of the sextortion emails, an additional point of personalisation is being included in the last sentence of the final paragraph that appears before the image of the victim’s address: “I don’t make mistakes, [first name.]” the email warns.
Criminals Are Leveraging Technology To Expedite Payment.
In some cases, quick response (QR) codes are being provided in the emails to make it faster and easier for victims to send bitcoin payments to the criminals. In the emails that include them, the QR codes appear directly below the bitcoin address.
Examples Of Sextortion Emails
Protecting Against Sextortion Scams
Sextortion emails are usually sent to thousands of people at a time as part of larger spam campaigns, so most get caught in spam filters. But attackers also vary and personalise the content of the emails, making them more difficult for spam filters to detect and stop.
Scammers are continually evolving their email fraud techniques, including using social-engineering tactics to bypass traditional email security gateways.
Sextortion emails that end up in inboxes typically do so because they originate from high-reputation senders and IPs; hackers use already-compromised Microsoft 365 or Gmail accounts.
Here are several ways to defend against sextortion scams:
AI-based protection — Attackers are continually adapting sextortion emails to bypass email gateways and spam filters, so a good spear-phishing solution that uses AI to detect and protect against these and other email attacks is a must.
Account-takeover protection — Many sextortion attacks originate from compromised accounts; be sure scammers aren’t using your organisation as a base camp to launch these attacks.
Deploy technology that uses AI to recognise when accounts have been compromised, allowing you to remediate in real time by alerting users and removing malicious emails sent from compromised accounts.
Proactive investigations — Given the nature of sextortion scams, employees might be less willing than usual to report these attacks due to the intentionally embarrassing and sensitive nature of the threats.
Conduct regular searches on delivered mail to detect emails related to password changes, security alerts, and other content. Many sextortion emails originate from outside North America or Western Europe. Evaluate where your delivered mail is coming from, review any of suspicious origin, and remediate.
Security-awareness training — Educate users about sextortion fraud, especially if you have a large and diverse user base. Make it part of your security awareness training program. Ensure employees can recognize these attacks, understand their fraudulent nature, and feel comfortable and know how to report them. Use phishing simulation to test the effectiveness of your training.
System maintenance — Keeping browsers and operating systems up-to-date helps prevent exploits from infecting computers. Sextortion emails can infect targets’ devices with malware, and keeping browsers and operating systems up-to-date prevents infection.
Related Resources
[Report] Top Email Threats & Trends ~ June 2024
https://www.barracuda.com/reports/email-threats-and-trends-1
[Glossary] Understanding sextortion and how to stay safe
https://www.barracuda.com/support/glossary/sextortion







