Internet connectivity for old devices in your home will end on Thursday.
A digital certificate widely used in electronic devices before 2017 will expire on September 30.
It is estimated that millions of gadgets around the world will be affected and will not be able to install updates to new digital certificates to allow continued connectivity to the Internet.
Devices that may have issues include older MacBooks and iPhones that can’t (or can’t) be updated with the latest software, some game consoles like PlayStation 3 and Nintendo 3DS, as well as smart TVs, decoders and IoT devices inside your home. House.
Anything that requires a secure connection to a specific server may stop working. Streaming platforms like Netflix, Stan, Binge and 7plus require users to have this secure connection. It can also affect any websites that require user login, such as email inboxes and banking websites.
Security researcher Scott Helme warned of this threat in June 2020 and visited his personal website again this week.
You may or may not need to do anything about it,” Helme wrote in his last blog post.
Thankfully there are a few workarounds that will allow you older dated devices to stay connected.
The Let’s Encrypt website has a feature for Android devices running Android Two (Gingerbread) or later until September 2024.
However, there are no fixes for any Mac running macOS 10.12.0 or earlier and cannot be officially updated by Apple. The same issue exists for iPhones and iPads that cannot be updated after iOS 9.
PlayStation 3 and 4 consoles with firmware prior to 5.00 will have connectivity issues, and if you are still using Windows XP with Service Pack 2 or earlier, we advise you to try updating them by Thursday if there are updates available.
Helme also notes that if you get stuck without any available updates, you should try to install the Firefox browser on your device, as Firefox does not use the operating system for security certifications and may provide additional access to certain sites.
But for other smart devices in the home that run on different operating systems, without an update for years and with no workarounds available, the end may be near.
Affected Clients
- OpenSSL <= 1.0.2
- Windows < XP SP3
- macOS < 10.12.1
- iOS < 10 (iPhone 5 is the lowest model that can get to iOS 10)
- Android < 7.1.1 (but >= 2.3.6 will work if served ISRG Root X1 cross-sign)
- Mozilla Firefox < 50
- Ubuntu < 16.04
- Debian < 8
- Java 8 < 8u141
- Java 7 < 7u151
- NSS < 3.26
- Amazon FireOS (Silk Browser)
Platforms still unsure
- Cyanogen > v10
- Jolla Sailfish OS > v1.1.2.16
- Kindle > v3.4.1
- Blackberry >= 10.3.3
- PS4 game console with firmware >= 5.00
- IIS
One of the notable clients that will still be affected by this process depends on the OpenSSL 1.0.2 or an earlier library, release January 22, 2015 and last update as OpenSSL 1.0.2u on December 20, 2019. OpenSSL has a blog – Post published detailing what actions those affected can take, but all of them require manual intervention to prevent breakage
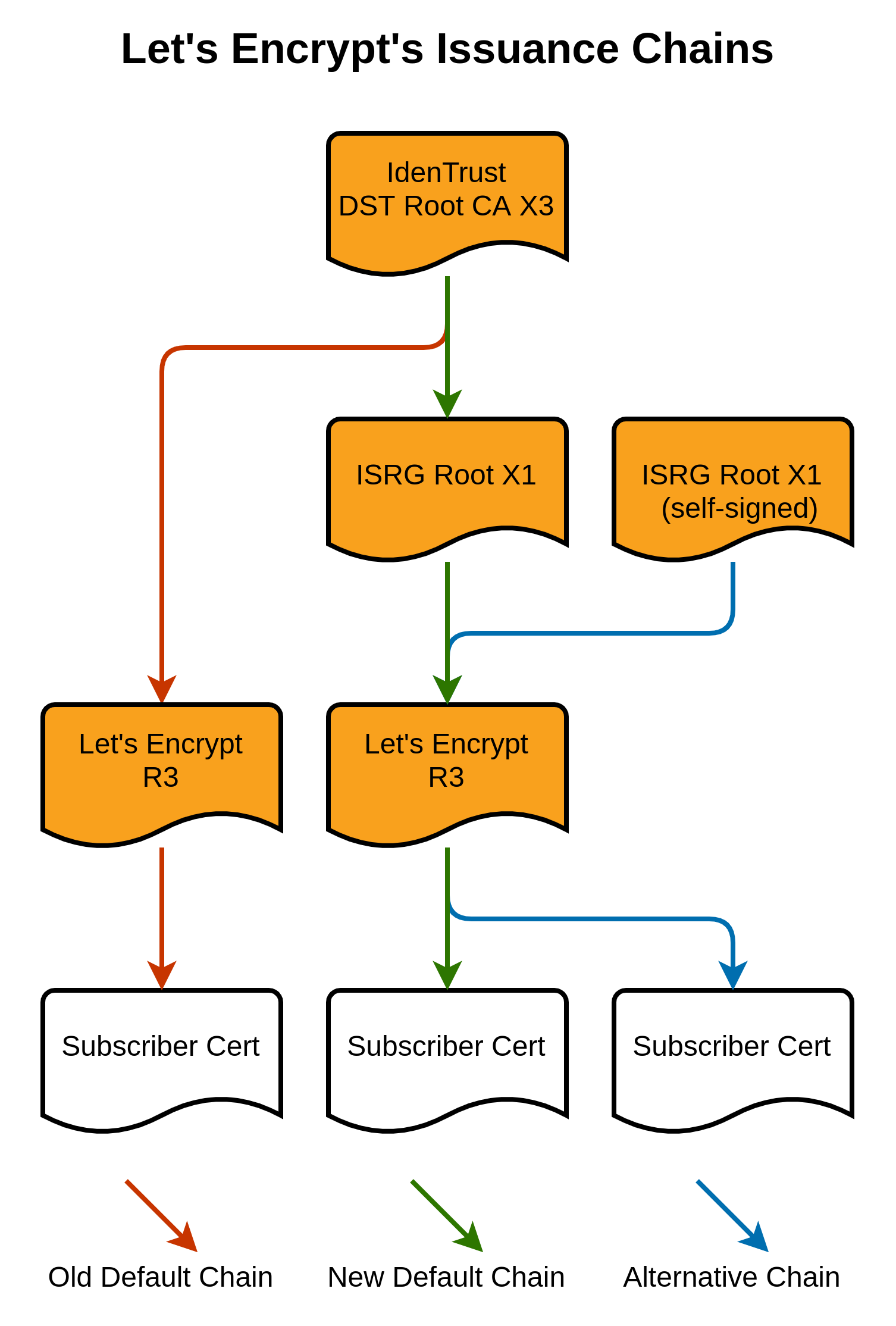
This is no the first time a root CA certificate has expired
This happened last year, May 30 at 10:48:38 2020 GMT to be exact, when the AddTrust external CA root expired and took a bunch of stuff with it. Organizations like Roku, Stripe, Spreedly and many others had issues and they weren’t the only ones, even RedHat had something to say about the event.
Security Certificates And SSL
When you talk about Internet security, one of the most important things to understand are the different types of security certificates which are available on the web today. For instance, a security certificate is issued by a trusted root CA certificate authority and serves as the gateway to an SSL certificate.
A SSL certificate, or session-keyed digital certificate, is used by the website visitor in order to validate that they have indeed visited a trusted website, and they are allowed to proceed with the transaction. This transaction is digitally signed with the private key stored in the website’s database server and served to the web browser via the URL.
The trust relationship between a website and its visitor is represented by the SSL certificate. A self-signed certificate on the other hand is a private key which is stored on the user’s PC, which can only be read by the user themselves, and represents a much lower level of security than both SSL encrypted certificates. However, a self-signed certificate cannot be used by anybody else to prove ownership of a domain or to establish responsibility for a given website. Instead, the user’s personal identification, commonly known as their username, is what is needed in order to access information on any website.
This fact also makes a self-signed certificate susceptible to man-in-the-middle attacks, where hackers can intercept the password and use it to gain access to a domain or even to the user’s account.
On the other hand, an SSL encrypted certificate can only be installed from certain trusted root certificates. These root certificates are issued by organisations which specialise in issuing SSL certificates.
These organisations can also install intermediate certificates between the user’s actual SSL private key and the root certificates. The intermediate certificates are used to ensure that the user’s privacy is protected while his actual private key is being installed on a computer.







