Within the APAC region, evasive bots were noted to constituting a substantial 71.1% of all malicious bot traffic. China demonstrated the highest prevalence of evasive bots at 86.5%, whereas Australia exhibited the highest incidence of advanced bots at 36.3%.
This class of sophisticated bots is adept at emulating human-like mouse movements and clicks, effectively confounding even the most sophisticated detection methods, rendering them the most formidable to combat.
Evasive bots are a new breed of malicious software designed to elude detection by security systems. Unlike traditional malware, these bots have evolved to bypass the most advanced security measures, posing a significant challenge to organisations and governments worldwide.
Accroding to director of technology, office of the CTO, Imperva, Reinhart Hansen Digitally mature nations such as China and Australia have more businesses and consumers transacting online.
“This makes them rich targets for cyber criminals. As digital maturity grows, bot operators are using more sophisticated scripts that can evade the common defenses,” he says.
“Businesses cannot overlook the impact of malicious bot activity as it is contributing to more account compromise, higher infrastructure and support costs, customer churn, and degraded online services,”
“With automated fraud growing in intensity and complexity, APAC organisations need to urgently implement advanced bot protection to safeguard their customers’ interests.” he says.
Imperva’s chilling revelation unveils a harrowing truth: bad bots, those sinister digital entities, are the ominous omens of online fraud, lurking in the shadows, ready to strike at the heart of digital enterprises and their unsuspecting patrons.
In the annals of 2021, a ghastly breed emerged – the evasive bad bots. A nefarious amalgamation of moderate and advanced malevolence, they shroud themselves in darkness, taunting standard security fortifications with their diabolical artistry.
They dance through the ether, evading capture by morphing through random IP addresses, masquerading behind the cloak of anonymous proxies, shedding and donning identities, and mimicking the very essence of human existence.
The global stage, a theater of darkness, witnessed their maleficent presence as they commanded 65.6% of all bad bot traffic, a somber testament to the peril that encircles the digital realm.
Evasive Bot Activites
Web scraping, competitive data mining, personal and financial data harvesting, scalping, account takeover fraud, spam and transaction fraud are just a few of the activities evasive bots play in 2023.
Overall 66% Of All Bad Bot Attacks Come From Russia & China
A study involving 440 businesses, carried out by Coleman Parkes and published by Netacea, a service specialising in artificial intelligence-driven bot detection, revealed that 53 percent of all bot attacks originated from Russia and China.
Specifically, 72 percent of the surveyed businesses reported encountering bots from China, while 66 percent experienced attacks from Russia.
Rob Black, an information activities lecturer at Cranfield University, has attributed this surge to the evolving landscape of warfare and conflict.
“In today’s age, conflict is no longer pursued solely through traditional military means. Instead, state actors are entering into a range of different forms of contest,”
“More often than not, these are enabled through rapid technological advancements, recognising that we are no longer distinct nations separated by borders and seas, but instead are interconnected through networks, information flows and data.” he said
Increasing tensions on the global stage, exemplified by the conflicts in Ukraine and strained relations between China and Western nations, could be potential drivers behind the rise in bot attacks originating from these countries.
According to Netacea co-founder Andy Still, while this geopolitical context might play a role, it remains challenging to pinpoint specific threat actors and their motivations definitively.
Nevertheless, Still added that, even if these attacks aren’t endorsed as official government policy, they tend to go unchecked within their respective regions because their outcomes align with broader national objectives.
Nick Hyatt, the leader of Optiv’s cyber practice, noted that automated attacks from Russia and China are hardly surprising. These nations possess advanced offensive security capabilities and adapt to the evolving landscape of intelligence operations.
Bad Bot Traffic
According to the 2022 Imperva bad bot report, Singapore had the highest proportion of bad bot traffic in the region at 39.1%, followed by China with 38.6%. Next came Australia (25.7%), New Zealand (20.3%) and Japan (16.9%)
Why Evasive Bot Detection Can Be Tough In 2023
Current bot protection measures have shortcomings, and it’s time to rethink bot detection for the future. Evasive bots are elusive, like Agent Smith in the Matrix, shapeshifting and adapting.
We need a new stateless approach to complement existing defenses. Here are the key mistakes in current bot protection:
- Obvious Defenses: Current bot mitigation services have conspicuous fingerprints, revealing the protection in use. It’s like advertising to criminals. It’s better not to disclose the defenses in place.
- Readable Code: Many bot defenses expose their client-side source code, providing a roadmap for bad actors to bypass them. It’s better to obfuscate the code, making it harder for attackers.
- Identifying Characteristics: Current solutions rely on specific identifying characteristics like IP, user agent, and behavior. When bots change these characteristics, detection becomes challenging. Stateless bot detection is a more robust approach.
- Overt Mitigation: Mitigation on the front end can give bad actors feedback they can use to adapt. Ideally, mitigation should be subtle, like a silent alarm or a dye pack, and occur on the backend while detection remains on the front end.
- Data Ownership: Bot detection companies often own the data generated during protection. This paradigm may shift as companies realize the value of their data, including security data. They should consider owning their data and being compensated for handling their bot traffic.
Reimagining bot detection for 2023 and beyond requires a shift towards stateless approaches, obfuscated code, inconspicuous defenses, backend mitigation, and data ownership.
Even Good Bots Can Be A Cause For Concern
Good bots have the potential to distort web analytics data, causing certain webpages to falsely appear more popular than they truly are. Take, for instance, the scenario in which a website advertises its products or services.
Good bots can also create impressions by clicking on these ads, but these clicks may not translate into actual conversions within the sales funnel. The consequence is a decrease in overall advertising performance.
Furthermore, this can introduce significant distortions into marketing analytics, which can, in turn, lead to misguided decision-making based on this skewed data. As a result, the ability to intelligently discern between traffic generated by legitimate human users, beneficial bots, and malicious bots becomes a critical factor in facilitating well-informed business decisions.
Accurate data is the bedrock upon which effective strategies are built, making the differentiation of bot-generated and human-generated traffic of paramount importance in the digital landscape.
Malicious Bots Are Affecting All Industries
Malicious bots pose a universal challenge that transcends industries and functional boundaries. because their capacity to execute a wide array of harmful actions at a speed and scale beyond human capabilities renders them a prime instrument for high-velocity abuse, misuse, and attacks.
While certain malicious bot applications, like content scraping and account takeover, are common across multiple sectors, there are also specific use cases tailored to particular industries, such as scalping, which predominantly impacts online retailers and the entertainment industry, particularly ticketing platforms.
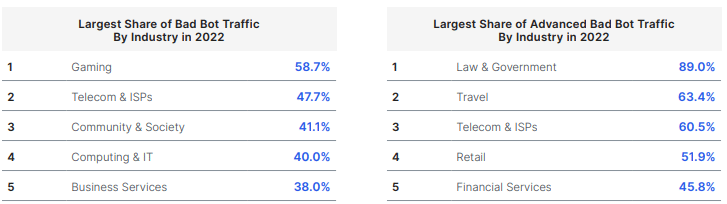
Most-Attacked Industries
It’s concerning to see that account takeover attacks were prevalent in various industries in 2022. Here’s a breakdown of the industries that experienced the largest volume of account takeover attacks:
- Financial Services: 37.8%
- This industry, which includes banks, credit card companies, and other financial institutions, was the primary target, with nearly 38% of all account takeover attacks occurring in this sector.
- Telecom & ISPs (Internet Service Providers): 17.2%
- Telecommunications and ISPs were also heavily targeted, with 17.2% of ATO attacks happening in this sector. This could potentially involve hijacking phone or internet accounts.
- Computing & IT: 15.6%
- The computing and IT industry, which encompasses technology companies, software providers, and IT services, experienced 15.6% of the account takeover attacks. This is particularly concerning given the sensitive data often handled by these companies.
- Food & Groceries: 8.5%
- Even the food and groceries industry was not spared, with 8.5% of ATO attacks. It’s essential for businesses in this sector to take cybersecurity seriously to protect both their operations and customer data.
Account Takeover Attacks (ATO)
Account takeover attacks (ATO) are persistently on the rise, driven by a combination of factors, including data breaches, new incentives, and the growing availability of bot infrastructure.
In 2022 alone, there were over 4,100 publicly reported data breaches, resulting in the exposure of around 22 billion records.
These breaches often serve as a catalyst for account takeover attacks, where malicious actors swiftly leverage the stolen credentials from these breaches before users become aware of the compromise.
A prime illustration of this relationship emerged in Q3 of 2022, when a staggering 70% surge in reported global data breaches coincided with a notable 40% uptick in account takeover attacks, as documented by Imperva during the same period.
Account takeover attacks can result in severe financial and reputational damage, making it imperative for organisations in these industries, as well as others, to implement robust security measures and educate their users about best practices to prevent such attacks.
Bad Bots Masquerading As Legitimate Users
Today, among the various tactics used by bad bots to elude detection, one prevalent strategy is concealing their true identity by posing as genuine users, presenting themselves as popular web or mobile browsers favored by humans.
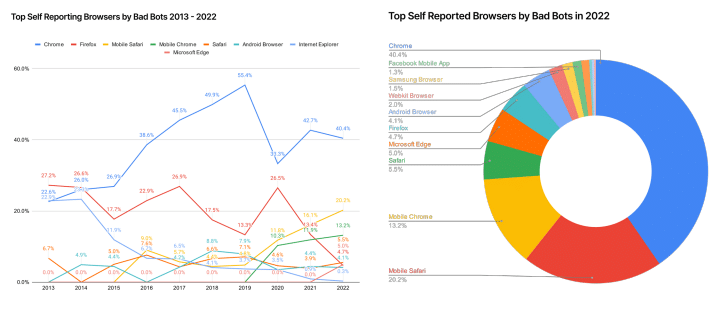
This deceptive maneuver is typically accomplished through the application of browser automation software. What initially constituted an advanced evasion technique a decade ago has now become commonplace among a majority, if not all, of malicious bots.
What adds an intriguing dimension to this scenario is how the preferences of these fraudulent bots for different browsers have evolved over the past decade. These transformations mirror not only the popularity of these browsers among human users but also other trends that assist bots in avoiding detection.
Of particular interest is the persistence of a trend we began monitoring last year – the growing favorability of bad bots selecting Mobile Safari as their preferred browser.
A noteworthy 20.2% of bot traffic now identifies itself as this browser, marking a significant increase from 11.8% in 2020 and 16.1% in 2021. It has become evident that these bots exploit the enhanced user privacy features provided by Mobile Safari to cloak their activities, rendering their detection even more challenging.
Conversely, the representation of bots masquerading as Chrome browsers witnessed a slight decline in volume, decreasing from 42.7% of traffic in 2021 to 40.4% in 2022.
In a similar vein, the utilisation of Mobile Chrome also saw an uptick, accounting for 13.2% of traffic, up from 11.9% in 2021.
Data Centers – The Weapon Of Choice
In previous years, data centers were the primary source of malicious bot traffic, accounting for 54% in 2020, which decreased to 45.1% in 2021. However, in the current year, there has been a notable increase in bad bots originating from data centers, rising by 13.5% to constitute 58.6% of all malicious bot traffic.
Despite a decline in the percentage of bad bots coming from residential ISPs, from 27.7% to 17.4%, we continue to observe a substantial presence of highly sophisticated bot campaigns emerging from these networks.
The proportion of traffic stemming from mobile ISPs has remained relatively consistent when compared to the previous year, with only a slight reduction from 27.2% in 2021 to 24.1% in 2022.
Evasive bots, designed to avoid detection and mimic human behavior, have become a formidable challenge for cybersecurity professionals worldwide.
The fact that China leads the pack in terms of their prevalence is both noteworthy and alarming. This statistic points to a complex interplay of factors, such as the nation’s technological prowess, its extensive internet user base, and the diverse motivations of these bots’ operators.
As China continues to be a major player in the tech world, its influence on the evasive bot landscape is undeniable. China boasts the highest penetration of evasive bots, with a staggering 86.5% of these automated entities infiltrating various online spaces.
This revelation raises significant questions about the evolving landscape of online security and the sophistication of malicious actors within the country. Or could it be global theat actors are simply using data centers in China due to lower regualtory standards to mount their attacks?







