What is a web browser and how do they work? – Web browsers are responsible for retrieving and displaying web content to users. When a user enters a URL or clicks on a link, the browser initiates a complex series of actions to retrieve the web content from a server and display it on the user’s device.
With the advent of the first graphical web browser in 1993 web browsers can now take you anywhere on the internet, letting you see text, images and video from anywhere in the world
In this article, I will provide a deep dive into the inner workings of web browsers and explore the various components that make them function.
What is a Web Browser?
A web browser is a software application that enables users to access and interact with web pages on the internet. It acts as an intermediary between the user and the web server, interpreting the HTML, CSS, and JavaScript code that makes up web pages and displaying the resulting content on the user’s screen.
The web browser’s primary function is to render web pages by processing the code and displaying the visual content in a readable format. Web browsers also allow users to navigate the web, bookmark pages, manage downloads, and perform other functions related to online activity.
Components of a Web Browser
A web browser comprises several components that work together to make it function. These components include:
- User interface – The user interface is the part of the web browser that the user interacts with. It includes menus, toolbars, and other graphical elements that allow users to navigate the web, manage bookmarks, and perform other functions. The user interface also displays the web page content to the user.
- Rendering engine – The rendering engine is responsible for processing the HTML, CSS, and JavaScript code that make up web pages and rendering them into a visual format that can be displayed on the user’s screen. Different browsers use different rendering engines, and each engine has its strengths and weaknesses.
- Networking – The networking component handles the communication between the web browser and web servers. When a user requests a web page, the networking component sends a request to the web server, and when the server responds, the networking component receives the data and passes it to the rendering engine for processing.
- JavaScript engine – The JavaScript engine interprets the JavaScript code that is embedded in web pages and executes it on the user’s device. JavaScript is a programming language that enables dynamic web page functionality, such as pop-up windows, animations, and interactive forms.
- User data storage – Web browsers store user data, such as bookmarks, browsing history, and login information, locally on the user’s device. This allows users to access their favorite websites quickly and easily.
The history of web browers.
In the early days of the internet, navigating the World Wide Web was a daunting task. Users had to rely on command-line interfaces and specialized software to access websites, and the experience was limited to text-based content.
This all changed in 1993 with the introduction of the first graphical web browser, Mosaic, developed by Marc Andreessen and his team at the National Center for Supercomputing Applications (NCSA).
Mosaic allowed users to:
- View images
- Play audio and video
- Navigate the web through hyperlinks.
The success of Mosaic paved the way for a new generation of web browsers, including Netscape Navigator and Microsoft Internet Explorer. These browsers dominated the market throughout the late 1990s and early 2000s, with each company vying for dominance in the emerging digital landscape.
The introduction of JavaScript in 1995 revolutionized web browsing, allowing for more interactive and dynamic web pages. This was followed by the introduction of Cascading Style Sheets (CSS) in 1996, which allowed for greater control over the visual appearance of web pages.
JavaScript was invented by Brendan Eich. It was developed for Netscape 2, and became the ECMA-262 standard in 1997
After Netscape handed JavaScript over to ECMA, the Mozilla foundation continued to develop JavaScript for the Firefox browser.
Emerging New Web Browsers
As the internet continued to grow and evolve, new web browsers emerged to meet the needs of users. Mozilla Firefox, launched in 2004, offered greater customization and security features than its predecessors, while Google Chrome, introduced in 2008, prioritized speed and simplicity.
Web browsing has become an integral part of daily life for billions of people around the world. From desktops to smartphones, we use web browsers to access information, connect with others, and explore new ideas.
Web Browser Security
Web browser security has become an increasingly important topic in recent years, as online threats have become more sophisticated and widespread. With billions of people around the world relying on web browsers for everything from online shopping to banking, the need for robust security measures has never been greater.
One of the biggest threats facing web browsers is phishing, a type of online scam in which criminals create fake websites that look like legitimate ones in order to steal sensitive information from unsuspecting users. In response, web browsers have implemented various security measures, such as anti-phishing filters, to protect users from these types of attacks.
Another common threat is malware, malicious software that can infect computers and steal data or cause other types of harm. Web browsers have implemented various security features to protect users from malware, such as sandboxing, which isolates web browser processes from the rest of the computer’s operating system.
In addition to these threats, web browsers must also contend with vulnerabilities in the underlying software that can be exploited by attackers. To address this, web browser developers regularly release security updates to patch these vulnerabilities and improve overall security.
Despite these efforts, web browser security remains an ongoing challenge. As attackers become more sophisticated and exploit new vulnerabilities, web browser developers must remain vigilant in their efforts to protect users.
To help mitigate these risks, there are several steps users can take to protect themselves. These include keeping web browsers and other software up to date, using strong passwords, and avoiding clicking on suspicious links or downloading unknown software.
Development of SSL & TLS Protocols
The SSL protocol and its successor, TLS, are critical components of modern web security. These protocols ensure that data exchanged between a web server and a user’s browser remains private and secure. In this article, we will discuss the history and development of SSL, as well as the mechanics of the HTTPS protocol that is now the standard for secure web browsing.
- History and Development of SSL
The SSL protocol was first introduced in the mid-1990s by Netscape Communications Corporation. At that time, there was a growing need for secure communication over the internet, as more and more sensitive information was being transmitted online. SSL was designed to provide encryption and authentication services for web traffic.
The first version of SSL, SSL 1.0, was never publicly released due to security flaws. SSL 2.0 was introduced in 1995 and quickly became the de facto standard for secure web communication. However, it too had significant security flaws, leading to the development of SSL 3.0 in 1996.
SSL 3.0 was a major improvement over its predecessor, offering stronger encryption algorithms and better handling of session keys. It was widely adopted and used for many years until it was replaced by the TLS protocol in 1999.
- Transport Layer Security (TLS)
TLS (Transport Layer Security) was developed by the Internet Engineering Task Force (IETF) as a successor to SSL. It was designed to address some of the weaknesses in SSL, particularly its vulnerability to attacks such as POODLE and BEAST. TLS is backward compatible with SSL, which means that web servers and browsers that support TLS can also communicate with those that support SSL.
In 1999, TLS was initially defined as a protocol independent of applications in RFC 2246. Although it was not compatible with SSL 3.0, it did provide a fallback mode in case of need. Nevertheless, SSL 3.0 is now deemed insecure and was deprecated by RFC 7568 in June 2015. It is recommended to use TLS 1.2 instead.
Sending and receive emails directly from web browsers – Webmail
The advent of web browsers revolutionized the way we interact with the internet, making it more accessible and user-friendly. One of the most significant impacts of this technology was the ability to send and receive emails directly from a web browser.
Before webmail, people had to rely on email clients installed on their computers, which required technical expertise to set up and manage. Additionally, email clients could be slow and difficult to use, especially for people who were not tech-savvy.
The introduction of web-based email services changed all that, making it possible for anyone to access their email from any device with an internet connection and a browser.
The first webmail service was launched in 1996 by Hotmail, which was later acquired by Microsoft and rebranded as Outlook.com. Hotmail allowed users to create a free email account, which could be accessed from any web browser. The service was an instant hit and quickly gained popularity, with millions of users signing up in its first year alone.
Soon after, other companies such as Yahoo and Google launched their own web-based email services, offering similar features and functionality. These services allowed users to send and receive emails, organise their messages, and even store attachments online.
One of the most significant advantages of webmail is its convenience. Users no longer need to install software or configure email clients to access their email. Instead, they can simply log in to their webmail account from any device and start sending and receiving messages immediately.
Another advantage of webmail is its accessibility. With webmail, users can access their email from anywhere in the world, as long as they have an internet connection. This made it easy for people to stay connected with friends, family, and colleagues, even when they are on the go.
Webmail services also typically offer large amounts of storage space, making it easy to store and access emails and attachments online. This is became especially useful for people who need to keep track of important emails or documents.
The introduction of web browsers to send and receive emails was a game-changer for the internet. It made email more accessible, convenient, and user-friendly, allowing people to stay connected with each other more easily than ever before.
Today, webmail services continue to evolve and improve, offering even more features and functionality to their users as technology continues to develop.
Web Brower Privacy & The Use Of Ingognito
Web browser privacy has become an increasingly important issue in recent years, as more and more people use the internet to shop, bank, and communicate sensitive information.
To protect their privacy, many web browsers now offer an “incognito” or “private browsing” mode that can help users browse the web more securely and privately.
When you use a web browser in its default mode, it stores information about your browsing history, cookies, and other data. This information can be used by websites and advertisers to track your activity and serve targeted ads.
Additionally, if someone else uses the same computer, they may be able to access your browsing history and other personal information
To address these concerns, web browsers offer an incognito mode that doesn’t save your browsing history, cookies, or other data. This can be especially useful when using a public computer or when accessing sensitive information such as online banking or medical records.
While incognito mode can be useful for protecting your privacy, it is not a foolproof solution. For example, it won’t prevent websites from tracking your activity while you’re on their site, and it won’t protect you from malware or other security threats.
Additionally, using incognito mode doesn’t necessarily mean that your browsing activity is completely private. Your internet service provider (ISP) can still see your activity, as can any websites you visit.
If you’re concerned about privacy, you may want to consider using a virtual private network (VPN) or other privacy tools in addition to incognito mode.
It’s also worth noting that while incognito mode can be useful for protecting your privacy, it can also have some downsides. For example, some websites may not function properly while you’re in incognito mode, as they may rely on cookies or other data to function correctly.
Additionally, incognito mode can make it more difficult to access certain features or settings in some web browsers.
Understanding Browsing history, Cookies & Cache
Web browsing history, cookies, and cache are all important components of the modern web browsing experience. Understanding how each of these works can help users to better manage their online privacy, as well as improve the speed and efficiency of their browsing sessions.
- Browsing History
Browsing history is a record of the websites that a user has visited. Most web browsers automatically track browsing history as users navigate the web. Browsing history can be useful for quickly returning to recently visited sites or for tracking down information that was previously accessed.
However, it can also be a privacy concern if the browsing history is accessible to others who may use the same device or network. To manage browsing history, users can typically clear it from their browser settings, or use private browsing modes that do not save browsing history.
- Web Browser Cookies
Cookies are small text files that are stored on a user’s computer or device when they visit a website. Cookies can be used for a variety of purposes, including remembering login credentials, tracking user preferences, and serving targeted advertisements.
While cookies can be useful, they can also be a privacy concern if they are used to track user activity without their knowledge or consent
- Web Browser Cache
Web browser cache is a temporary storage space on a computer or mobile device that stores recently visited web pages and their associated files, such as images, scripts, and stylesheets.
When a user revisits a webpage, the browser can quickly retrieve the page and its files from the cache rather than having to request them again from the server, which can improve page loading times and reduce bandwidth usage. However, if the cached content is outdated or the user needs to access the most recent version of a page, they may need to clear their browser cache.
Use of Proxy Servers For Web Browsing
We rely heavily on the internet for everything from socializing to shopping, from education to entertainment. But with this increased reliance comes increased vulnerability, as our personal information is transmitted and stored online. One way to protect ourselves while browsing the web is through the use of a proxy server.
A proxy server is an intermediary between a user’s computer and the internet. When a user requests a web page, the request is sent to the proxy server, which then retrieves the page from the internet and forwards it to the user. The website being accessed sees the request as coming from the proxy server, not the user’s computer, which provides some degree of anonymity and security.
There are several reasons why someone might choose to use a proxy server for web browsing. One of the most common is to protect their privacy. By using a proxy server, a user’s IP address and other identifying information is hidden from the websites they visit. This can prevent tracking and profiling by advertisers, as well as protect against hackers and other malicious actors who might be trying to exploit vulnerabilities in the user’s system.
Another reason to use a proxy server is to bypass internet censorship or geo-restrictions. In some countries, access to certain websites or content is restricted by the government.
By using a proxy server located in a different country, users can bypass these restrictions and access the content they want. Similarly, some websites or streaming services may only be available in certain regions due to licensing agreements.
Proxy servers can also be used to improve network performance. By caching frequently accessed pages and files, proxy servers can reduce the amount of data that needs to be transmitted over the network, which can lead to faster load times and lower bandwidth usage.
- Proxy Server Drawbacks
While there are certainly benefits to using a proxy server, there are also some potential drawbacks. One of the biggest is that the proxy server itself can potentially see all of the user’s internet activity, including passwords and other sensitive information. This is why it’s important to use a reputable proxy server provider that takes privacy and security seriously.
Another potential drawback is that using a proxy server can sometimes result in slower web browser speeds, particularly if the server is located far away from the user’s location. Additionally, some websites may not function properly when accessed through a proxy server, which can be frustrating for users.
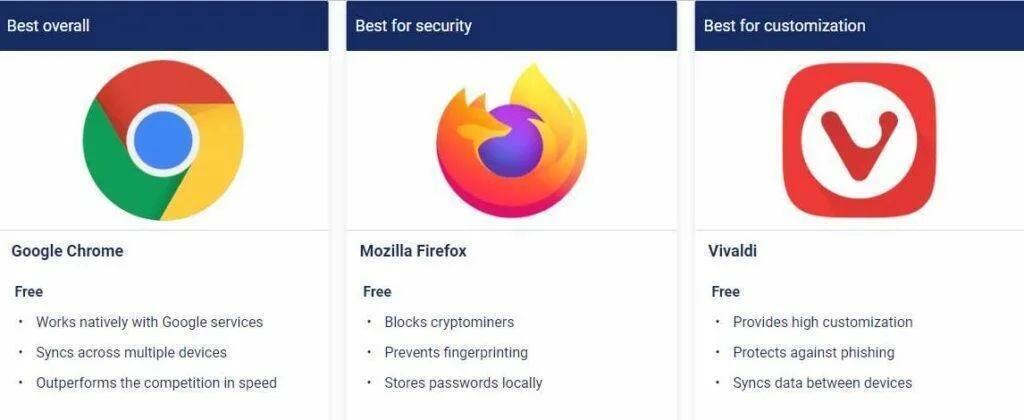
The 6 Best Web Browsers
According to highspeedinternet.com these are the 6 best web broswers in 2023
- Best overall: Google Chrome
- Best for security: Mozilla Firefox
- Best for customization: Vivaldi
- Best for social media: Opera
- Best for macOS: Apple Safari
- Best for Windows: Microsoft Edge
Introduction To DNS & It’s Use In Web Browsing
The Domain Name System (DNS) is a critical component of the internet infrastructure that allows us to access websites using human-friendly domain names instead of IP addresses.
The DNS acts as a directory that translates domain names like google.com into the corresponding IP addresses like 172.217.6.174 that computers and other devices use to identify each other on the internet.
It is essentially a giant phone book for the internet. When you type a domain name into your browser, your computer sends a request to a DNS server to translate that name into an IP address.
The DNS server then checks its cache to see if it has the IP address already, and if not, it sends a request to another DNS server higher up in the hierarchy. This process continues until a DNS server is found that can provide the IP address for the domain name.
The DNS hierarchy is composed of several layers. At the top of the hierarchy are the root servers, which are maintained by organizations such as ICANN and Verisign.
These servers store information about the top-level domains (TLDs) like .com, .org, and .net. Below the root servers are the TLD servers, which store information about the individual domains within each TLD.
- History of DNS
Before DNS, accessing websites required the use of numeric IP addresses. This was difficult for users to remember and communicate, and it also made it hard for website owners to change their server’s IP address without causing disruption to their users.
In the early days of the internet, a file called the “hosts” file was used to map domain names to IP addresses. This file was manually updated and distributed among all computers on the network. However, as the internet grew and the number of computers on the network increased, this approach became impractical.

In the 1980s, computer scientists Paul Mockapetris and Jon Postel developed DNS as a distributed, hierarchical database that would allow for the automatic resolution of domain names to IP addresses. The first implementation of DNS was introduced in 1983, and it quickly became an essential part of the internet’s infrastructure.
- DNS Caching
DNS caching is an important aspect of the system, as it helps to reduce the load on the DNS servers and speed up the process of translating domain names into IP addresses. DNS servers can cache the results of previous requests, so if multiple users request the same domain name, the server can provide the IP address from its cache instead of sending a new request up the hierarchy.
When a DNS server receives a request for a domain name, it first checks its cache to see if it has the IP address already. If not, it sends a request to one of the root servers to find out which TLD server is responsible for the domain name. The TLD server then directs the DNS server to the authoritative name server for the domain name, which provides the IP address.
- DNS Security
Despite its importance, the DNS system faces several challenges. One of the biggest is security. DNS servers are vulnerable to attacks such as DNS spoofing and DNS cache poisoning, which can cause users to be directed to fraudulent websites.
To mitigate these risks, DNSSEC (DNS Security Extensions) has been developed to add digital signatures to DNS records, ensuring that they are authentic and have not been tampered with.
The TCP/IP Protocol & Web Browsing
The Transmission Control Protocol/Internet Protocol (TCP/IP) is a set of protocols that are used to establish communication between devices over the internet. TCP/IP is responsible for the smooth functioning of the internet, and it is the foundation of all internet communication. One of the most popular applications that rely on the TCP/IP protocol is web browsing.
To access a web page, a user needs a web browser, which is a software application that can send and receive information over the internet. The web browser communicates with the web server using the TCP/IP protocol.
- The URL (Uniform Resource Locator)
When a user types a URL (Uniform Resource Locator) into the address bar of a web browser, the browser sends a request to the web server using the HTTP (Hypertext Transfer Protocol) over TCP/IP. The request includes the URL of the web page, and the web server responds with the requested page. The web browser receives the response and displays the web page to the user.
The TCP/IP protocol plays a crucial role in ensuring that the data transfer between the web browser and the web server is reliable and error-free. The TCP protocol breaks the data into smaller packets and assigns a unique number to each packet. These packets are then transmitted over the internet to the destination device.
These packets may take different routes to reach the destination, and they may arrive out of order. However, the TCP protocol ensures that all packets are received and reassembled in the correct order.
- The IP Protocol
The IP protocol, on the other hand, is responsible for routing the packets to their destination. Each device connected to the internet has a unique IP address, which is used to identify the device.
When a packet is sent from a source device to a destination device, it may pass through several routers and switches before reaching its destination. The IP protocol ensures that the packets are routed to the correct destination device based on its IP address.
Slow Loading Web Pages
In today’s highly connected world, where internet speed and convenience are highly valued, a slow-loading web page can be frustrating and detrimental to user experience. There are several reasons why a web page may load slowly:
- Large file sizes One of the most common reasons for slow-loading web pages is large file sizes. This could be due to high-resolution images, videos, or bulky code. Large files take longer to download and can significantly slow down the loading time of a page.
- Server problems Another reason for slow-loading web pages could be server problems. If the server is overloaded or not responding, it will take longer for the web page to load.
- Browser cache A browser cache is a temporary storage location on the user’s computer where previously downloaded files are stored to speed up future visits to the same web page. However, if the browser cache is overloaded, it can slow down the loading time of a web page. Clearing the cache can help resolve this issue.
- Poor hosting A web page’s hosting can also impact its loading speed. Poor hosting can result in slow response times and downtime, which can significantly affect the browsing experience.
Methods Used To Accelerate Web Browsing Performance
Whether you’re scrolling through social media, reading news articles, or shopping online, you want your web browsing experience to be fast and efficient. However, with so much data being transferred over the internet, web browsing performance can sometimes be sluggish.
Here are some of the methods used to accelerate web browsing performance:
- Use a modern web browser:
One of the simplest ways to accelerate web browsing performance is to use a modern web browser. Modern web browsers, such as Google Chrome, Mozilla Firefox, and Microsoft Edge, are designed to be faster and more efficient than older browsers. They also have features like tab management, ad-blockers, and built-in password managers that can further enhance your browsing experience.
- Clear your browser cache:
Your browser cache stores temporary files that are used to speed up your browsing experience by storing frequently accessed web page elements. However, over time, this cache can become cluttered, which can slow down your browsing experience. Clearing your browser cache regularly can help to speed up your browsing experience by freeing up space for new data to be stored.
- Disable unnecessary browser extensions:
Browser extensions can be a great way to enhance your browsing experience, but too many extensions can slow down your browser. If you have a lot of extensions installed, try disabling the ones you don’t use regularly. This will free up resources and help to speed up your browsing experience.
- Use A Fast DNS Provider & Content Delivery Network (CDN)
A content delivery network (CDN) is a system of servers that are designed to deliver web content to users quickly and efficiently. CDNs work by caching web content on servers that are located closer to the user, which can significantly reduce load times.
DNS services like Cloudflare’s 1.1.1.1 or Google’s 8.8.8.8 can speed up your browsing by providing faster and more reliable DNS resolution.
Overall, using a fast and reliable DNS service can speed up your browsing experience by reducing latency and providing better availability. Cloudflare’s 1.1.1.1 and Google’s 8.8.8.8
Browser Audio
The HTML5 audio element allows audio files to be embedded directly into web pages, enabling users to play audio content within the browser. This was a significant advancement in web audio, as it eliminated the need for external media players and enabled a more seamless user experience.
With the introduction of HTML5 audio, developers began to experiment with new and innovative ways of using audio in web applications. Audio was used for everything from background music on websites to interactive audio-based games and applications.
One notable example of audio being used in web applications is the game “AudioSurf.” This game, released in 2008, allows players to navigate a course created by their own music library. The game analyses the audio file and generates a unique track for the player to navigate, creating a new and interactive experience based on the user’s music preferences.
Today, audio capabilities in web browsers have advanced even further. Web Audio API, introduced in 2011, allows for real-time audio processing and manipulation directly in the browser.
The introduction of audio capabilities in web browsers has significantly expanded the creative potential of web development. From background music on websites to interactive music videos and games, audio has become an integral part of the web browsing experience.
Browser Video
The incorporation of video content into web browsers became an essential component of the online experience
In 1995, Netscape Navigator 2.0 introduced the <EMBED> tag, which enabled developers to embed media, including video, directly into web pages. This was a significant breakthrough, as it allowed users to view video content without having to leave their browser or download a separate player. However, there were limitations to the technology, and users still had to download the video file before they could view it.
In 1999, the World Wide Web Consortium (W3C) released the first version of the HTML 4.0 specification, which included the <VIDEO> tag. This new tag made it possible for developers to embed video directly into web pages, without the need for a separate player or plugin. However, the technology was not widely adopted, and many users still had to download video files before they could view them.
- Adobe Flash Player
The widespread adoption of video on the web began in 2005, with the release of Adobe Flash Player. This plugin enabled developers to create interactive and engaging video content, including animations and games, that could be viewed directly within web browsers. Flash quickly became the dominant technology for web video, and it remained so until the mid-2010s.
Video in web browsers has come a long way since its early beginnings. From the first experiments with Video for Windows to the widespread adoption of HTML5, video has evolved into an essential component of the online browsing experience
Extended Summary – Conclusion
Web browsers are the primary tools used by people to access the internet and browse web content. Invented in the early 1990s, web browsers have since evolved to become sophisticated pieces of software capable of handling complex web applications and rich multimedia content.
The history of web browsers is a fascinating one, with early browsers such as Mosaic and Netscape Navigator paving the way for modern browsers like Google Chrome and Mozilla Firefox.
The browser wars of the late 1990s and early 2000s saw intense competition between Microsoft’s Internet Explorer and Netscape Navigator, with Microsoft ultimately emerging as the dominant player.







